Foreword
In Windows Server 2025, Microsoft added the ability to secure computer accounts with Credential Guard, in addition to user and service accounts. These accounts are crucial for maintaining the security of Kerberos and service accounts. To reverse this setting, the domain join process must be repeated.
When computers are part of a domain, they are assigned an account in Active Directory and must authenticate using a password that is automatically generated and updated.
If the password becomes invalid after restoring the computer, the error message “The trust relationship between this workstation and the primary domain could not be established” will appear.
Enabling machine identity isolation allows for virtualization-based protection of AD machine accounts. When enabled, the machine account credentials of the device will be relocated into Credential Guard. As a result, all future machine account authentications, such as logging into a domain-joined device, will be routed through Credential Guard. However, if Credential Guard fails to start after a device reboot, it results in the inability to complete domain authentication, potentially requiring intervention from a local administrator account to recover.
Prerequisites
- Windows Server 2025
- You need to have Credential Guard configured. For information to this topic, check my blog article about it: https://theadmincafe.ch/p/configure-credential-guard-windows/
Create GPO
Open your Group Policy Management and do a right-click on the “Group Policy Objects” folder and select “New”.

Choose a good name for the GPO.

Do a right-click on the newly created GPO and select “Edit”.

Navigate to the following path:
Computer Configuration -> Policies -> Administrative Templates -> System -> Device Guard
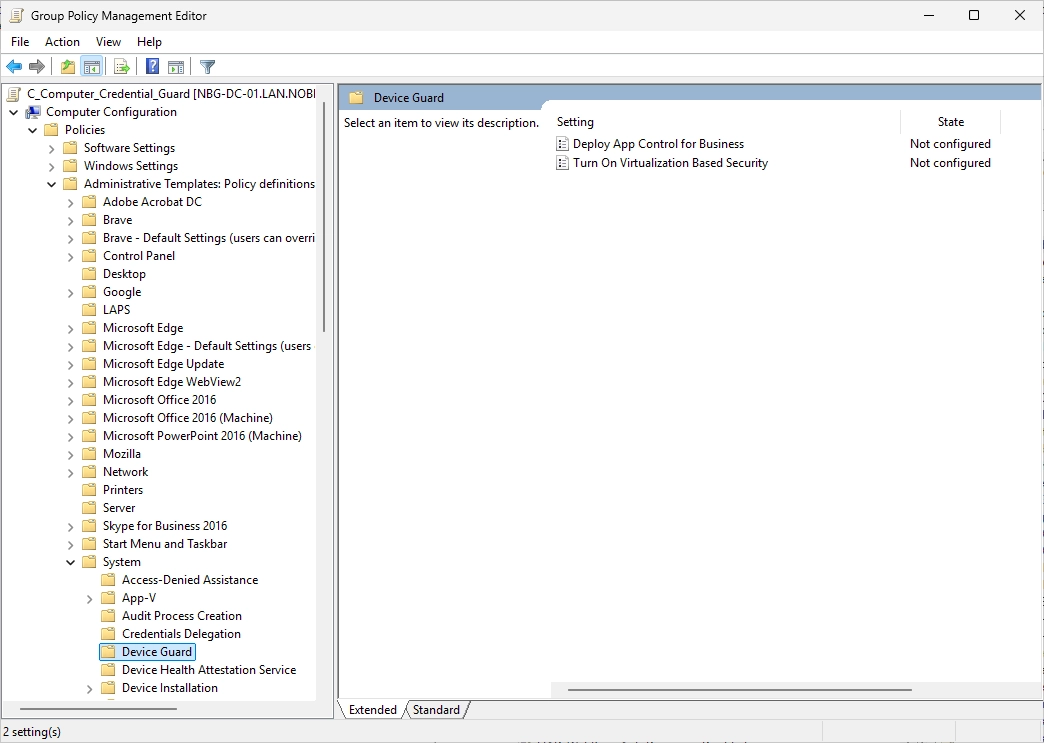
Do a right-click on the “Turn On Virtualization Based Security” option and select “Edit”.

The following window appears.

The option we need is “Machine Identity Isolation Configuration”.
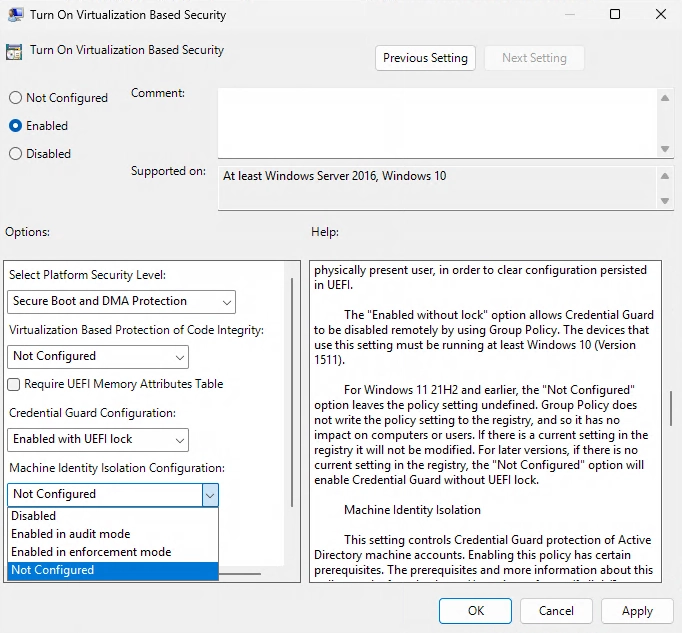
Enabled in audit mode
This option creates a new secret in Credential Guard and copies it into the Local Security Authority (LSA). The old LSA secret is then deleted. When auditing, attempts to authenticate the machine identity will first try to use the copy in Credential Guard. If that fails, authentication falls back to using the original machine identity from LSA.
Info: If the policy was previously set to enforcement mode, the device must be manually unjoined and rejoined.
Enabled in enforcement mode
This option moves the machine account secret into Credential Guard and deletes it from LSA. This makes the machine account secret inaccessible except as utilized by Credential Guard for machine authentication.
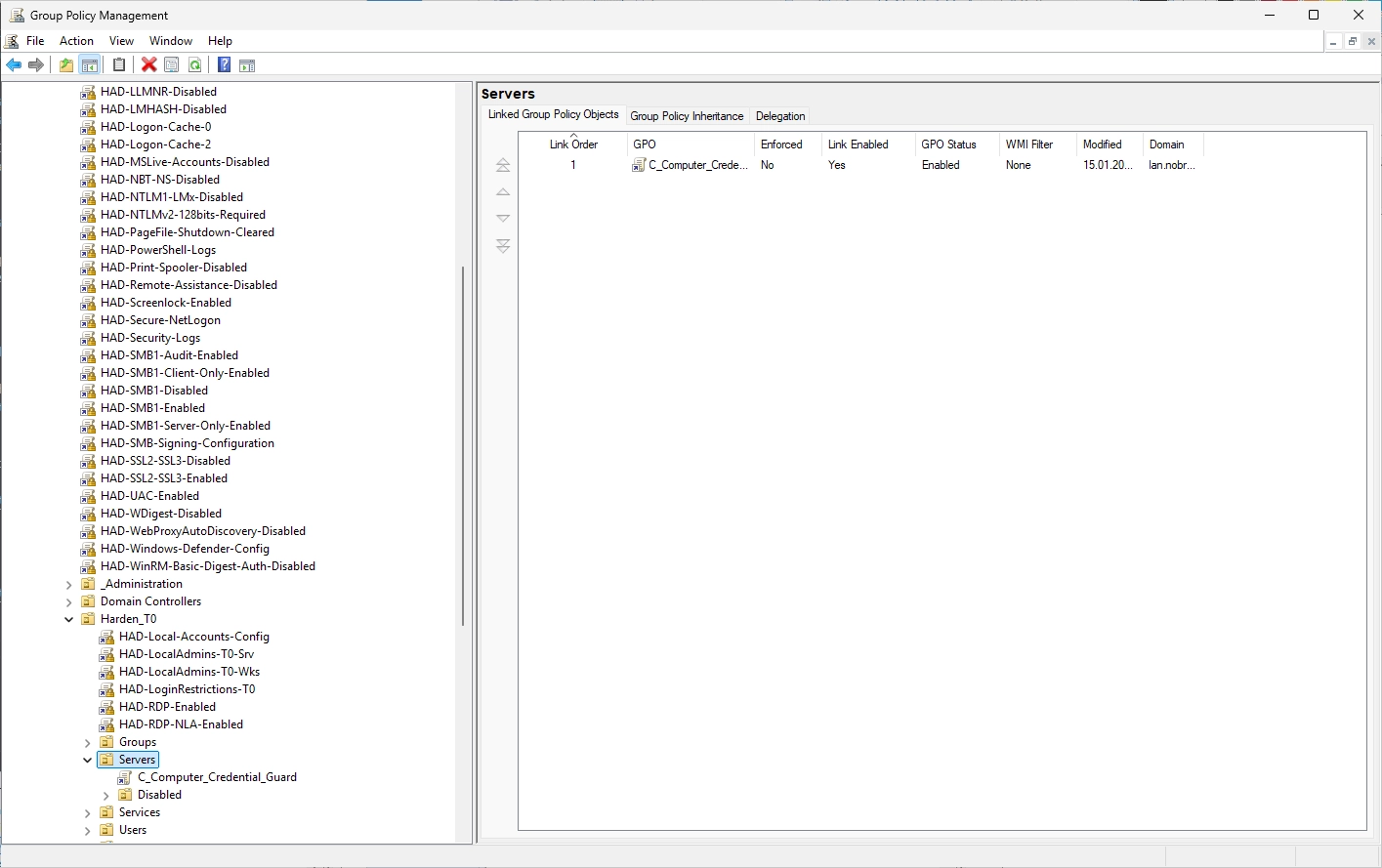
Link the GPO
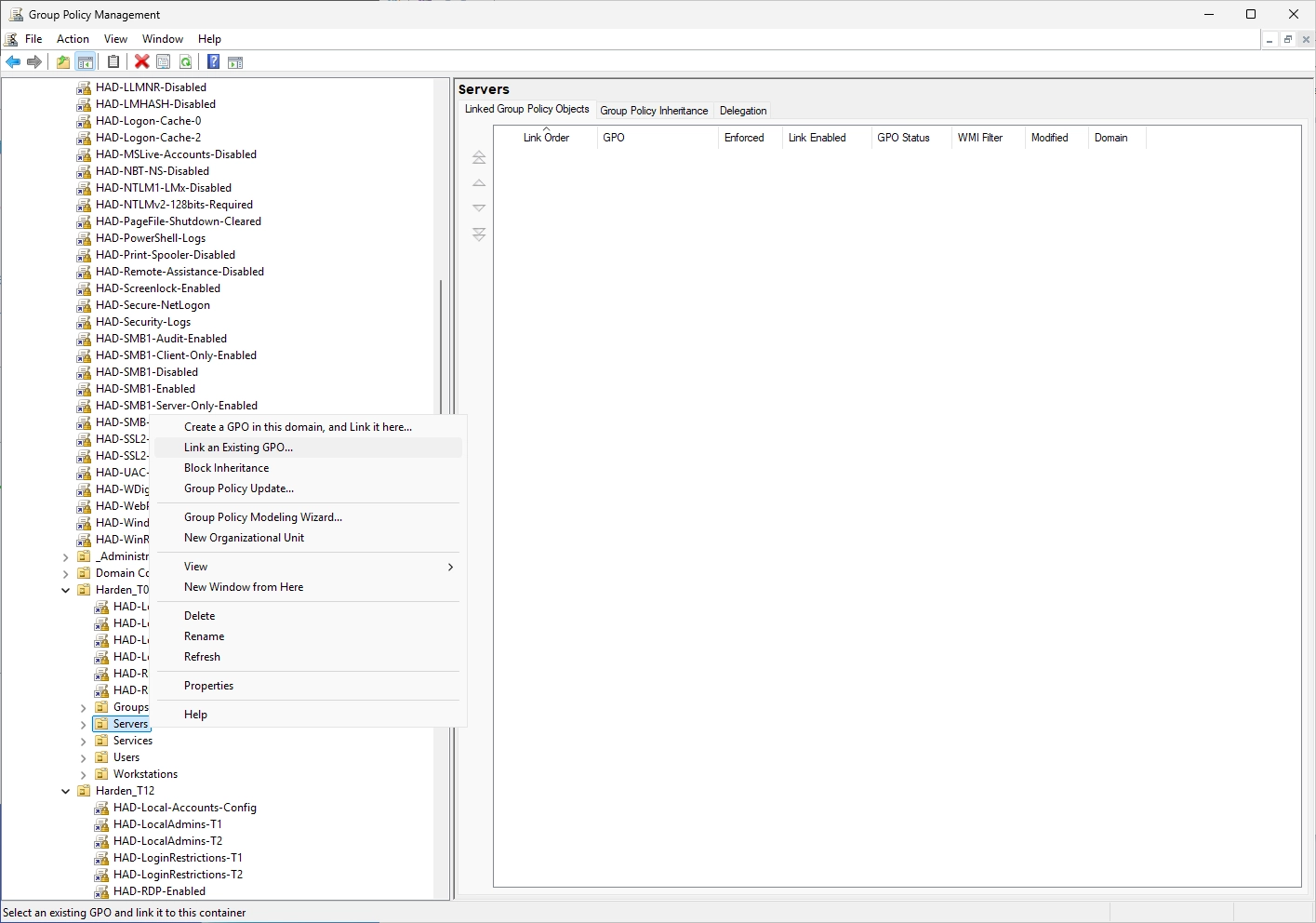
Link the GPO to the servers where the machine account is to be protected by Credential Guard. In this example I link the GPO to my T0 Server OU.
Da a right-click on the OU and select “Link an Existing GPO…”.
Select your newly created GPO.
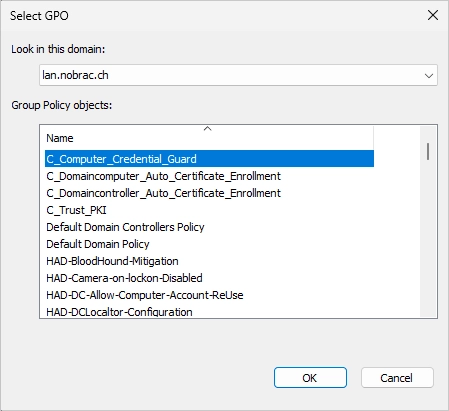
You should then see your linked GPO in the overview.
Then restart the computer or server for the changes to take effect.
Conclusion
So why is this important?
Recent Windows features, such as the Flexible Authentication Secure Tunneling (FAST) Kerberos extension—also referred to as Kerberos Armoring—have become increasingly reliant on machine accounts to boost security. The machine account adds entropy to the client’s secret key, and both gMSA and dMSA service accounts now depend on machine accounts, granting them access to service accounts. However, this dependence on machine accounts introduced a security vulnerability, as machine accounts can be easily extracted from the registry and exploited to access highly protected service accounts.
The security of machine accounts is reinforced, ultimately strengthening the overall security of service accounts within Active Directory.
