Foreword
OSConfig is a new feature in Windows Server 2025 that enables the configuration of security settings recommended by Microsoft. These settings are largely aligned with those in the Security Baseline. Management can be performed through PowerShell, Windows Admin Center, or Azure Policy, and OSConfig can automatically address any deviations from the desired configurations.
Historically, Microsoft has provided its recommended security settings in the form of exported GPOs, which can be selectively or fully imported into an environment.
This security baseline includes templates for various roles and features, such as member servers, domain controllers, Defender Antivirus, and Credential Guard. However, despite the release of Windows Server 2025 over two months ago, it is not yet included in the Security Compliance Toolkit for the operating system.
While OSConfig in Windows Server 2025 follows a similar approach, it does not rely on group policies. Instead, it uses a PowerShell interface for local management, and a dedicated service monitors and corrects any discrepancies from the intended settings.
Install OSConfig-Module
You can install the Powershell OSConfig-Module with the following command:
|
|

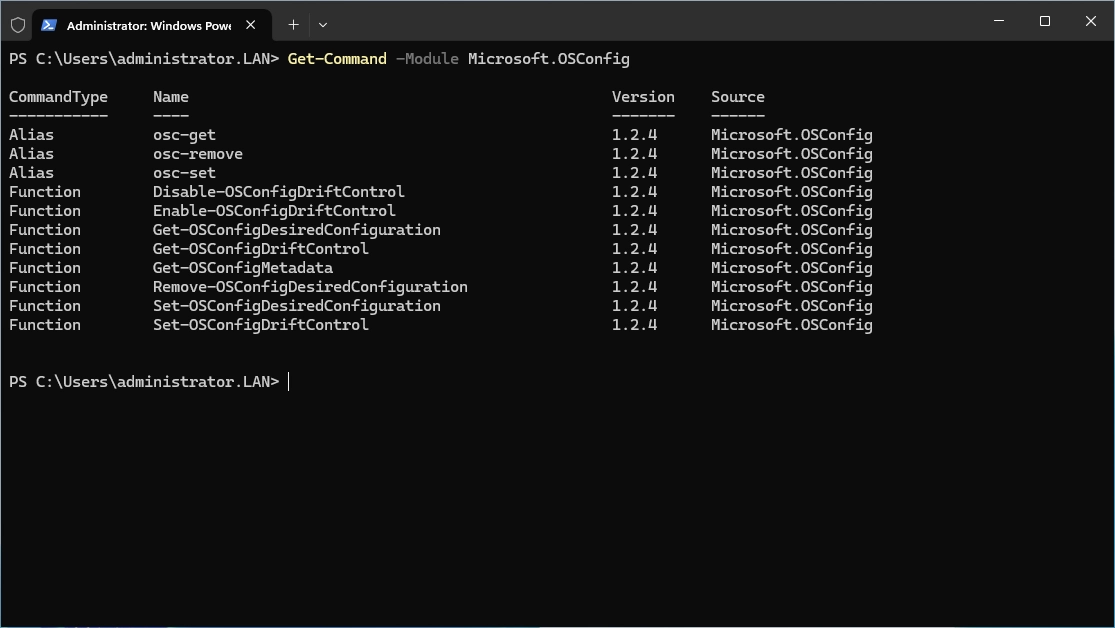
The available commands of the Powershell module can be displayed with the following command:
|
|
List Templates
To find out which templates are available for the security settings in OSConfig, enter the following command:
|
|

Besides the templates for member servers and domain controllers featured in the Security Baseline, OSConfig also provides templates for AppControl, Secured Core, and workgroup servers. The primary target group for OSConfig is likely to be workgroup servers, as Active Directory domains are managed centrally through group policies.
Enable a Baseline
While the GPOs from the security baseline can be customized before being applied to target computers, OSConfig generally operates in the opposite way.
With OSConfig, you enable a scenario that includes all settings and then selectively deselect the ones you don’t need. Although it’s possible to enable individual settings one by one, this approach is usually impractical due to the large number of settings involved.
Customization is often necessary because enforcing a strict security configuration can sometimes cause issues with applications or other systems within the network.
This command displays the settings included in a template along with the values assigned to them:
|
|

As shown in the command output, Get-OSConfigDesiredConfiguration is primarily used to assess the status of the desired configuration and highlight any discrepancies.
In our example, the settings for Defender Antivirus are displayed, all marked as “NotCompliant” because the relevant baseline has not been activated yet.
To configure the settings, Set-OSConfigDesiredConfiguration is used, as shown in the example for Defender Antivirus:
|
|
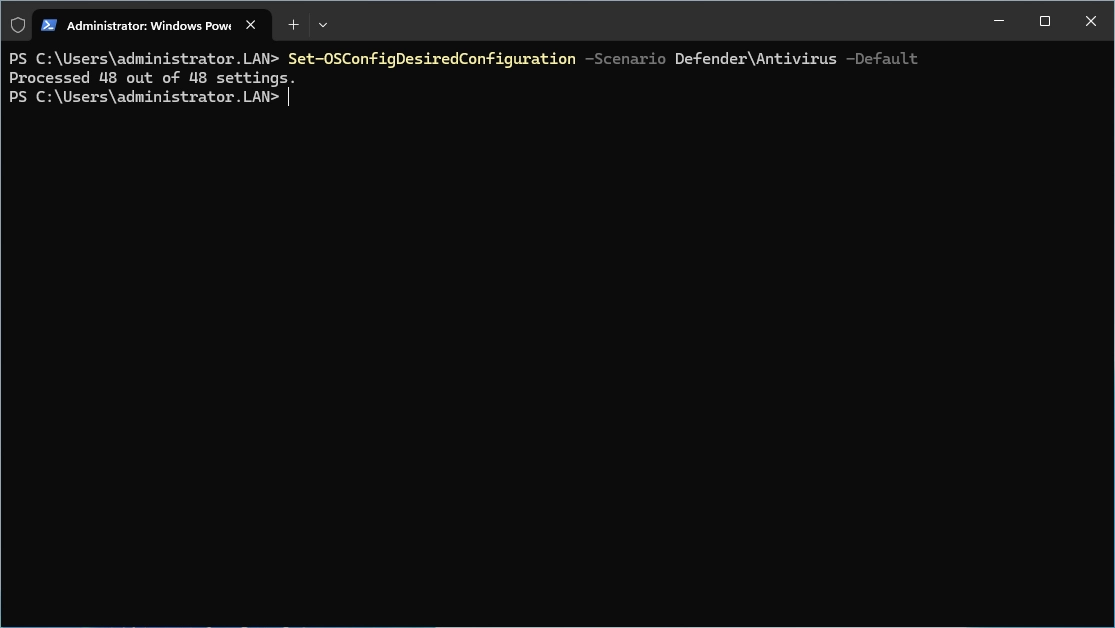
The “Default” parameter ensures that all settings from the template are applied. Alternatively, the “Setting” parameter can be used to configure individual settings. One of these two parameters must always be provided.
To change a specific setting, proceed as follows:
|
|

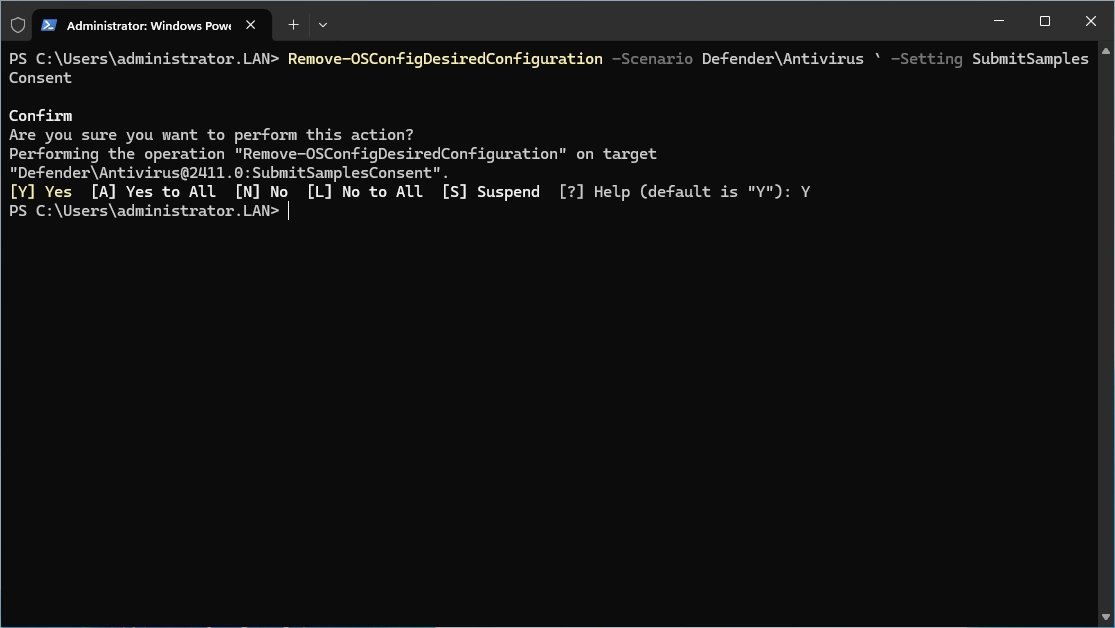
If you wish to not only change a setting but also remove it, you can use the following command:
|
|
You can also remove the complete baseline with the following command:
|
|

Applying or removing a baseline requires a server reboot for the changes to take effect. Adjusting some settings also requires a restart sometimes. Additionally, deleting a baseline does not ensure that the previous configuration will be restored. Make sure to always have Snapshots/Backups before you test!
