Foreword
In this guide I will show you how to configure Modsecurity for the IIS webserver with the OWASP rules.
Download Modsecurity
Download Modsecurity from the official Github page. The latest version for Windows is v2.9.7 at the moment. Just download the MSI-File.
Link: https://github.com/owasp-modsecurity/ModSecurity/releases/tag/v2.9.7

You should now have the downloaded file.
Double click to install it and follow the setup. Click on next.

Accept the terms and click on next.
Just click on next again.
Make sure that the option “Perform ModSecurityIIS configuration.” is selected (should be default).
Click on install.
Click on finish.
Confirm installation
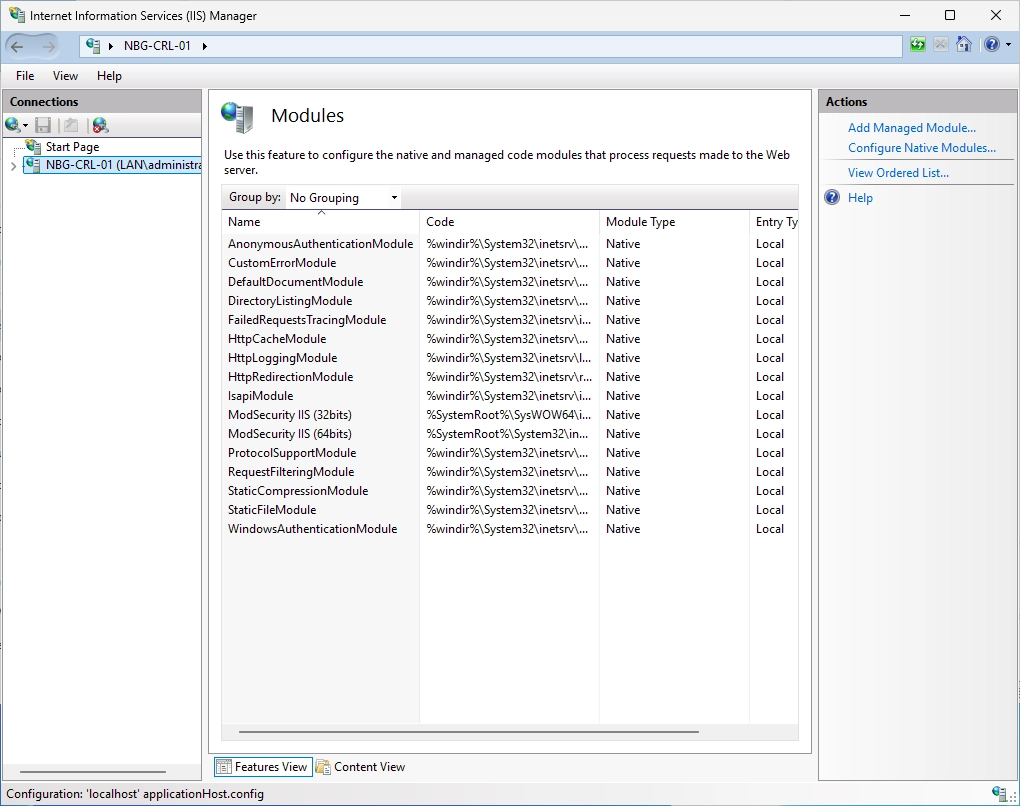
Open the IIS Manager on your IIS server.

Select the “Modules” option. You should see entries for “ModSecurity” like in the screenshot below.
Download OWASP rules
Download the OWASP core ruleset from the official Github page. Just download the minimal ZIP-File.
Link: https://github.com/coreruleset/coreruleset/releases/tag/v4.10.0
Navigate to the following path:
|
|
Find the “modsecurity.conf” file.
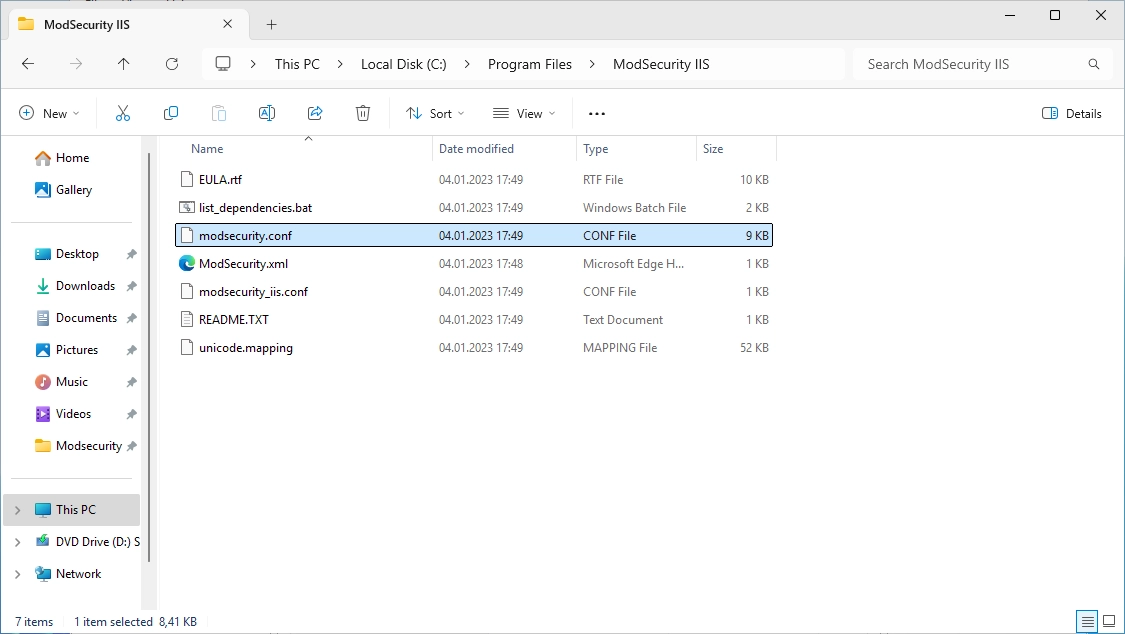
Open the file with the editor of your choice.

Change the line “SecRuleEngine” to enable it.
|
|
It should look like this.

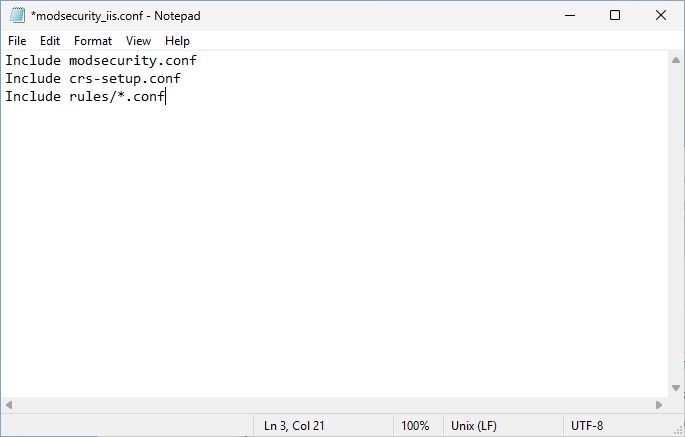
Now find the “modsecurity_iis.conf” file.

Open the file with the editor of your choice and add the following lines:
|
|
It should look like this:
Open the extracted core ruleset folder and search the file “crs-setup.conf.example”.

Copy the file to the “ModSecurity IIS” folder.

Remove the “.example” file type. It should look like this.

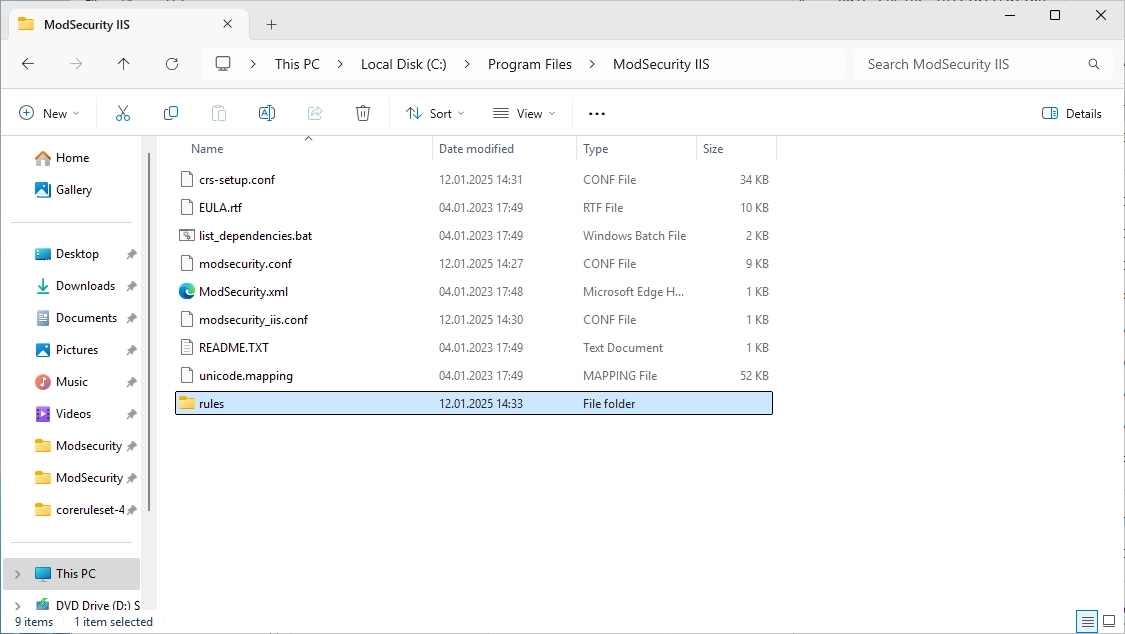
Open the extracted core ruleset folder and search the “rules” folder.

Copy the “rules” folder to the “ModSecurity IIS” folder. It should look like this.
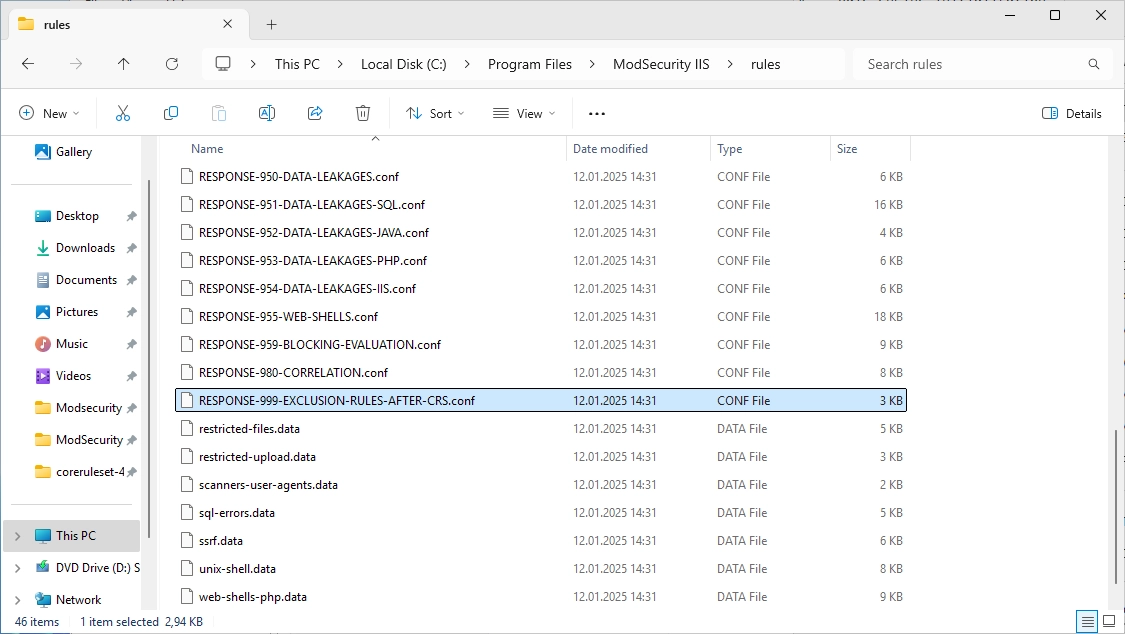
Now go into the “rules” folder and search the “RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example” file.

Remove the “.example” file type. It should look like this.
In the C:\ directory, create a new folder with the name “Modsecurity-Logs”.

It should look like this.

Do a right-click on the new folder and select “Properties”.
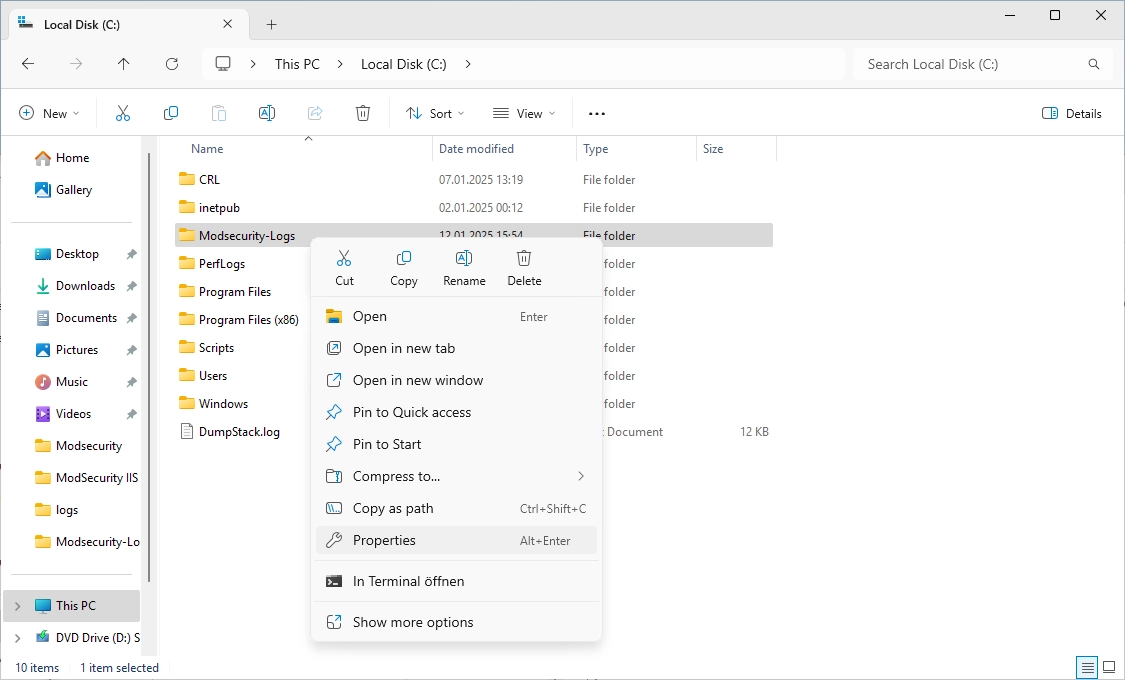
The following window appears.

Navigate to the “Security” tab and click on “Edit…”.
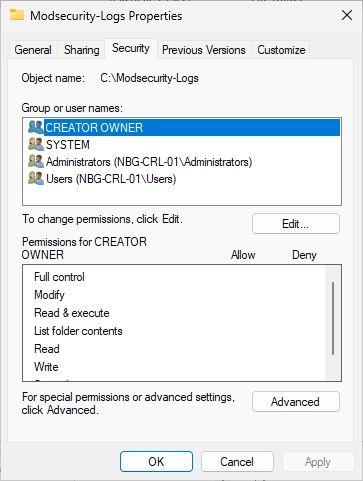
The following window appears. Click on “Add…”.
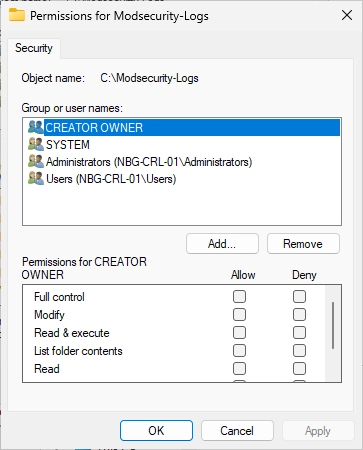
You should see the following window. Click on “Locations…”.
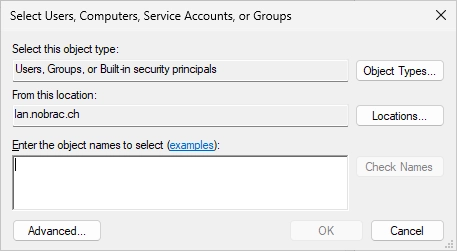
Select your IIS server.
Select the “IIS_IUSRS” group.
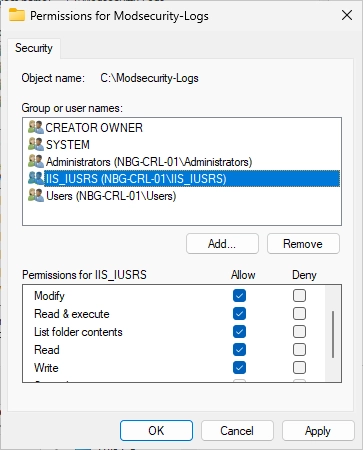
Make sure that you give the “IIS_IUSRS” modify permissions. It should look like in the screenshot.
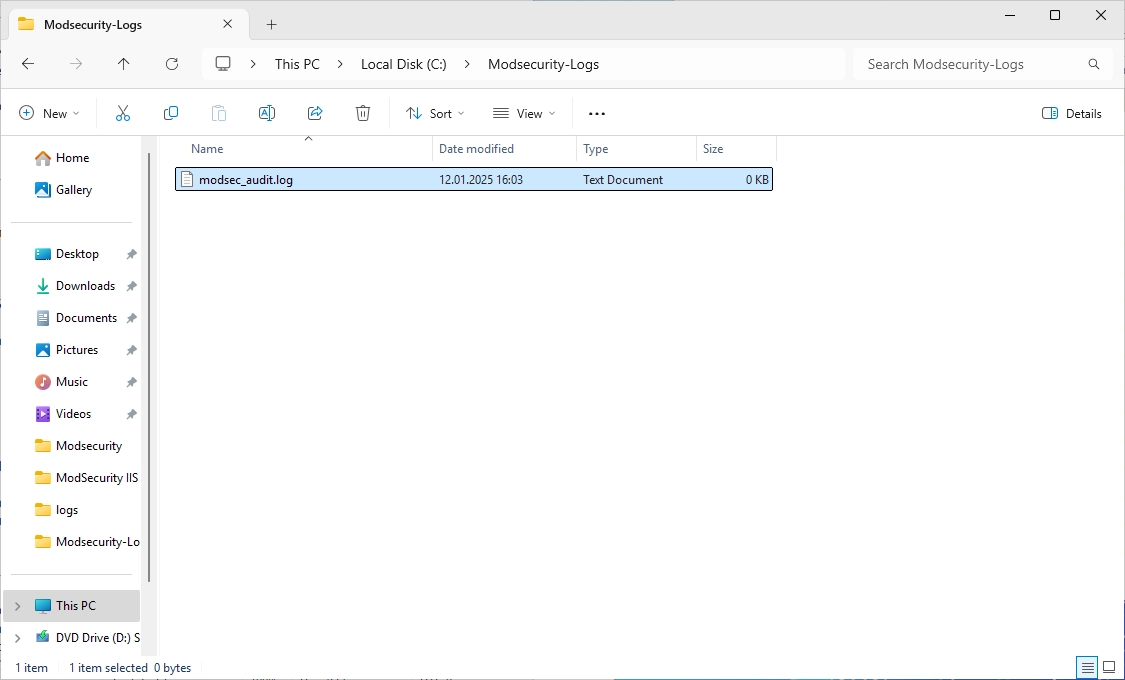
In the new “Modsecurity-Logs” folder, create a new Text Document.

Change the name of the file to “modsec_audit.log” and accept the warning cause of the file name extensions change.

It should look like this in the end.
Navigate to the “ModSecurity IIS” path and open the “modsecurity.conf” file again.
|
|
Scroll down until you find the “SecAuditLogType” option.
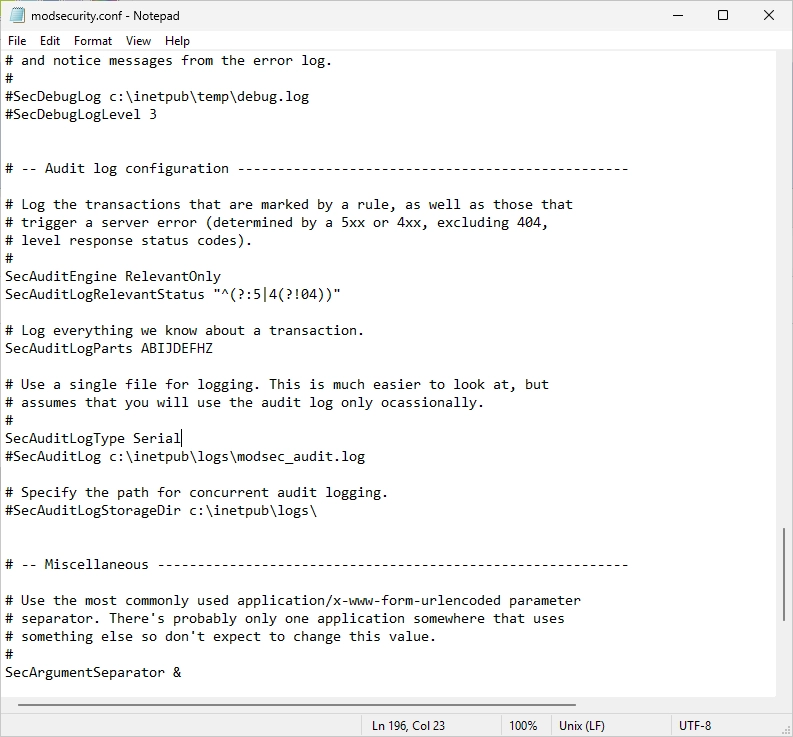
Remove the “#” symbol at the “SecAuditLog” option and change the path to “C:\Modsecurity-Logs\modsec_audit.log”.
It should look like this.
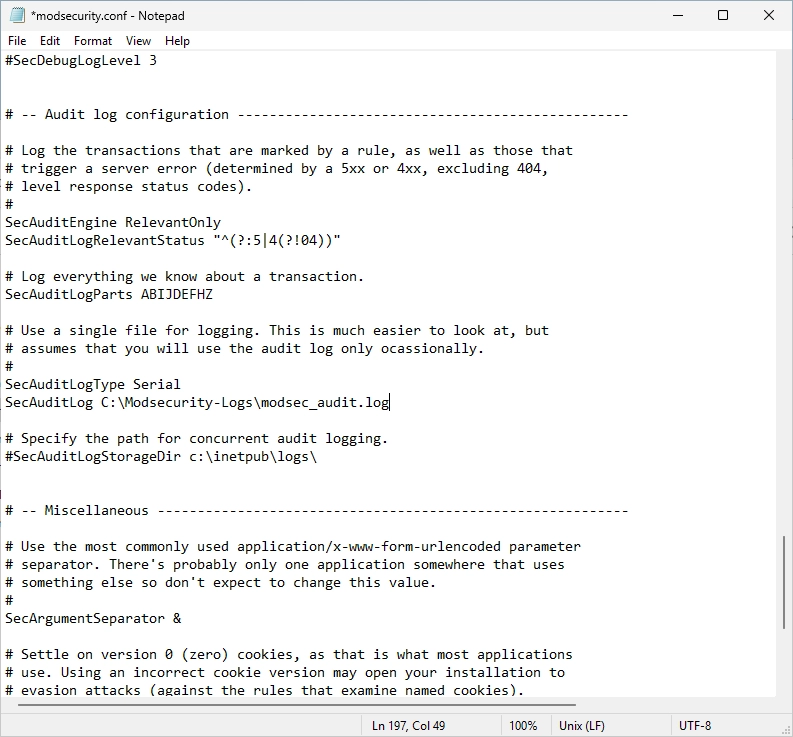
Restart the IIS after that.

Test
To confirm that Modsecurity works we can do a little test.
From an external client, enter the published Domain of the your IIS and enter /etc/passwd/ as the path. We should get a 404 error.

We should now see an entry for this in the “modsec_audit.log” file. Modsecurity has now been successfully tested.

Fix PKI (CertEnroll)
If you operate a PKI, it is very likely that access to the /CertEnroll directory will no longer work. There are entries in the log that could look something like the ones below.

If you try to access the /CertEnroll folder you probably get an access denied or blank page.

Navigate to the C:\Program Files\ModSecurity IIS\rules folder and search the “REQUEST-920-PROTOCOL-ENFORCEMENT.conf”.

Scroll at the bottom of the file and insert the following lines:
|
|
It should look like this.

Restart the IIS after the change.

The access should work again after the restart.

